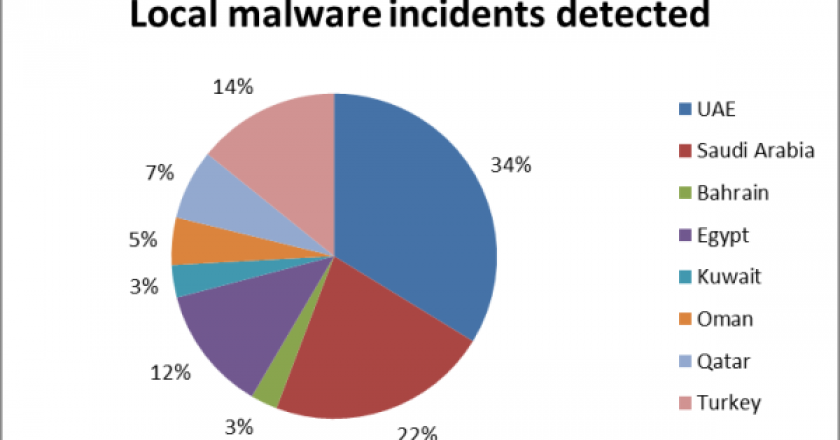
When it comes to security, it seems everyone’s in a state of perpetual panic. Whether it’s mobile malware, BYOD or hacktivism, over the course of 2013 the issue of protecting valuable information and resisting attack has inspired a dizzying and persistent challenge.