Matthew Brownlie has more than a decade of executive leadership experience and expertise in driving operational improvements and scaling businesses for growth.


Matthew Brownlie has more than a decade of executive leadership experience and expertise in driving operational improvements and scaling businesses for growth.

Microsoft Azure customers worldwide now gain access to WSO2 Asgardeo to take advantage of the scalability, reliability and agility of Azure to drive application development and shape business strategies.

Lisa Wee, Global Head of Sustainability – AVEVA, tells CNME Editor Mark Forker about the role the industrial leader is playing in driving sustainability across the industry – the role AI can play in mitigating emissions, the need to validate data – and how we can create a net-zero mindset.

Kingston Technology insists latest counter-infringement products can repel threats and ensure hospitals and staff ‘protect the data they are entrusted with’.

Report Uncovers Value of Network Investments in Improving Store Operations; Highlights Growing Consumer Demands for In-Store Mobile Experiences.

Strategic initiatives like Nafis, Dubai Economic Agenda ‘D33’, and UAE Net Zero 2050 are strengthening the UAE’s healthcare value chain.
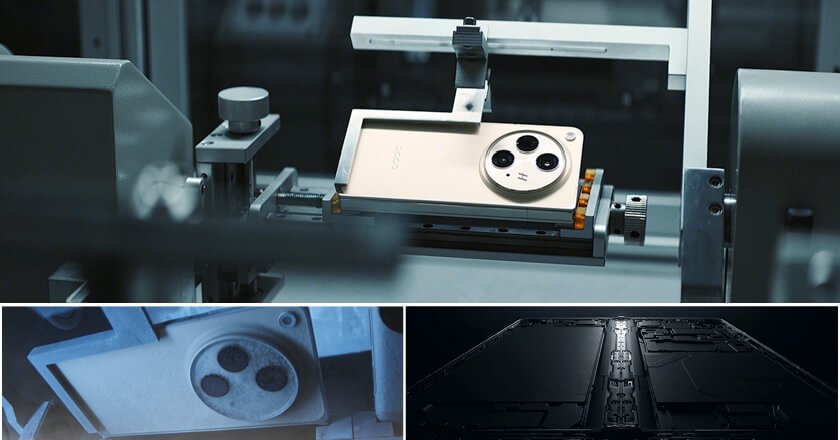
Leveraging engineering mastery, OPPO introduces the next-generation foldable device, featuring a groundbreaking Flexion Hinge with a Torque Control System.
The key technological trends that we see affecting the security sector in 2024 reflect this rapidly evolving environment. As ever, they’re a mix of positive opportunities to be grasped, alongside the challenges that need to be addressed.

Nearly 9 in 10 people (88%) said that just 50% or less of their digital transformation (DX) projects completed in the past year achieved the expected goals or outcomes, which has impacted the employee experience.

The VRC Initiative establishes a set of standardised rules and processes to enable institutions to compensate their solid waste footprint through a transparent ecosystem.

Kicking-off the alliance, Mindware will be furnishing sales and pre-sales skilled resources to ensure the correct positioning of the Vectra AI platform.

The VAST Data Platform Version 5.0 Adds New AI-Based Event Detection, Real-Time Monitoring and Simple Provisioning Tools for AWS Hybrid Cloud Deployments.

Attackers and bad actors will go to any lengths to get your data and hard-earned cash using techniques including phishing emails and mobile texts containing links to fake websites designed to look like legitimate brands.

Samer Seman, Channel and Alliances Manager – MEEA at Pure Storage, moderates a conversation with Hussam Baafeef, Channel Manager, Saudi & Bahrain at Pure Storage, and Mario M. Veljovic, General Manager at VAD Technologies during Pure Accelerate in Riyadh, earlier this month.