Kaspersky has detected and blocked over 142 million phishing link clicks globally in Q2 2025, the UAE saw a 21.2% increase from Q1 in phishing attempts.
Currently phishing is going through a shift driven by sophisticated AI-powered deception techniques and innovative evasion methods. Cybercriminals are exploiting deepfakes, voice cloning and trusted platforms like Telegram and Google Translate to steal sensitive data, including biometrics, electronic signatures and handwritten signatures, posing unprecedented risks to individuals and businesses.
AI-powered tactics transforming phishing attacks
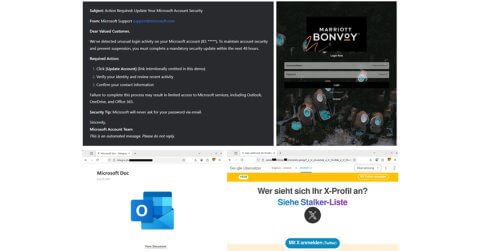
AI has elevated phishing into a highly personalised threat. Large language models enable attackers to craft convincing emails, messages and websites that mimic legitimate sources, eliminating grammatical errors that once exposed scams. AI-driven bots on social media and messaging apps impersonate real users, engaging victims in prolonged conversations to build trust. These bots often fuel romantic or investment scams, luring victims into fake opportunities with AI-generated audio messages or deepfake videos.
Attackers also create realistic audio and video deepfake impersonations of trusted figures — colleagues, celebrities or even bank officials — to promote fake giveaways or extract sensitive information. For instance, automated calls mimicking bank security teams use AI-generated voices to trick users into sharing two-factor authentication (2FA) codes, enabling account access or fraudulent transactions. Additionally, AI-powered tools analyse public data from social media or corporate websites to launch targeted attacks, such as HR-themed emails or fake calls referencing personal details.
Employing new tactics to bypass detection
Phishers are deploying sophisticated methods to gain trust, exploiting legitimate services to prolong their campaigns. For instance, Telegram’s Telegraph platform, a tool to publish long texts, is used to host phishing content. Google Translate’s page translation feature generates links that look like https://site-to-translate-com.translate.goog/… and are used by attackers to bypass security solutions’ filters.
Attackers now also integrate CAPTCHA, a common anti-bot mechanism, into phishing sites before directing users to the malicious page itself. By using CAPTCHA, these fraudulent pages deflect anti-phishing algorithms, as the presence of CAPTCHA is often associated with trusted platforms, lowering the likelihood of detection.
A switch in hunting: from logins and passwords to biometrics and signatures
The focus has shifted from passwords to immutable data. Attackers target biometric data through fraudulent sites that request smartphone camera access under pretexts like account verification, capturing facial or other biometric identifiers that cannot be changed. These are used for unauthorised access to sensitive accounts or sold on the dark web. Similarly, electronic and handwritten signatures, critical for legal and financial transactions, are stolen via phishing campaigns impersonating platforms like DocuSign or prompting users to upload signatures to fraudulent sites, posing significant reputational and financial risks to businesses.
“The convergence of AI and evasive tactics has turned phishing into a near-native mimic of legitimate communication, challenging even the most vigilant users. Attackers are no longer satisfied with stealing passwords — they’re targeting biometric data, electronic and handwritten signatures, potentially creating devastating, long-term consequences. By exploiting trusted platforms like Telegram and Google Translate, and co-opting tools like CAPTCHA, attackers are outpacing traditional defences. Users must stay increasingly sceptical and proactive to avoid falling victim”, said Olga Altukhova, security expert at Kaspersky.
Detailed information is available in a report on Securelist.com.
Earlier in 2025 Kaspersky detected a sophisticated targeted phishing campaign which was dubbed Operation ForumTroll, as attackers sent personalized phishing emails inviting recipients to the “Primakov Readings” forum. These lures targeted media outlets, educational institutions and government organisations in Russia. After clicking on the link in the email, no additional action was needed to compromise their systems: the exploit leveraged a previously unknown vulnerability in the latest version of Google Chrome. The malicious links were extremely short-lived to evade detection and in most cases ultimately redirected to the legitimate website for “Primakov Readings” once the exploit was taken down.
To be protected from phishing, Kaspersky recommends:
- Verify unsolicited messages, calls, or links, even if they appear legitimate. Never share 2FA codes.
- Scrutinise videos for unnatural movements or overly generous offers, which may indicate deepfakes.
- Deny camera access requests from unverified sites and avoid uploading signatures to unknown platforms.
- Limit sharing sensitive details online, such as document photos or sensitive work information.
- Use Kaspersky Next (in corporate environments) or Kaspersky Premium (for individual use) to block phishing attempts.
Image Credit: Kaspersky





