Learn how the cyber variety of CSI works, from sizing up the crime scene and hunting for clues to piecing together the story that the data has to tell.


Learn how the cyber variety of CSI works, from sizing up the crime scene and hunting for clues to piecing together the story that the data has to tell.

The UAE has forged a global reputation for being one of the most innovative countries in the entire world. It …

Doros Hadjizenonos, Regional Director at leading cybersecurity specialists Fortinet, outlines the growing number of fraudsters present within online dating apps.
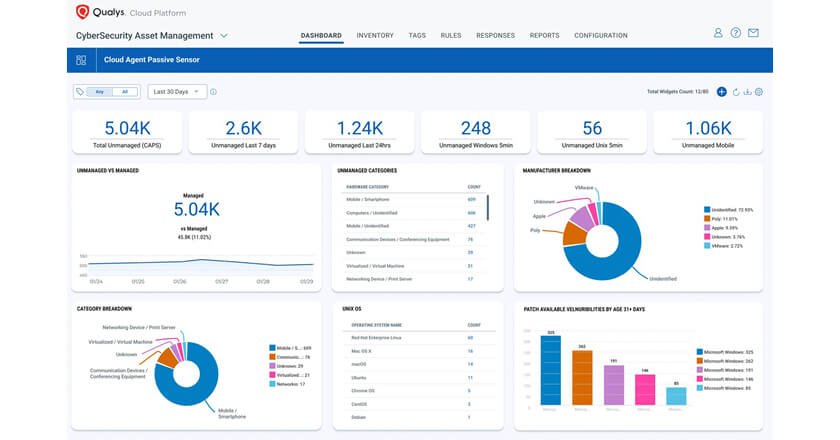
Groundbreaking functionality enables millions of cloud agents to discover risky unmanaged devices in real time with one click.
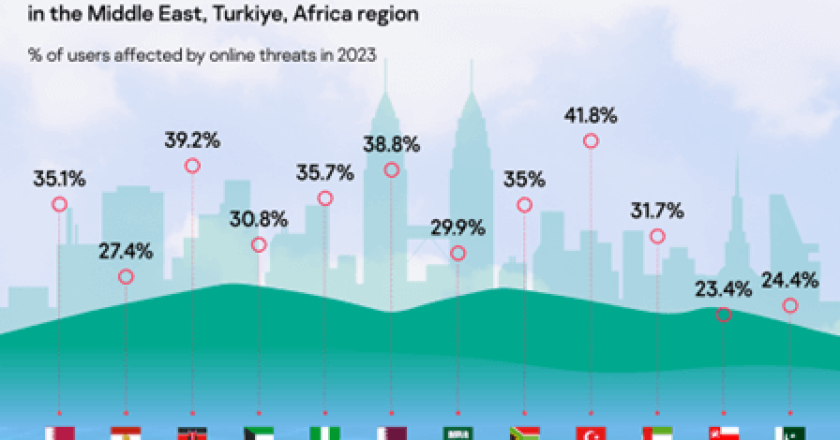
In 2023, Kaspersky reported 6% growth in B2B sales in the Middle East region and successfully blocked a total of …

Shining a spotlight on the laundering of cryptocurrencies, Chainalysis has revealed that such activity fell sharply, by nearly 30% last …

Tenable Warns of Cupid’s Deception as Deepfakes and Generative AI Amplify Romance Scams.

Emad Fahmy is currently the Systems Engineering Manager at NETSCOUT. In this op-ed he discusses how packet data can support the crucial task of protecting digital landscapes from cybersecurity threats.

By adopting a comprehensive cybersecurity strategy, financial institutions can effectively protect their systems, safeguard sensitive customer data, and maintain their …

After a Two-Year Investigation, Sophos X-Ops Discovers Unprecedented Sophistication in Scams That Trick Victims into Fake Investments.

Every day is Safer Internet Day. With data being the soul of businesses as well as virtual and vulnerable, it …

Expert instructors from SANS Institute will host specialized training in ICS security, as well as the latest threat hunting and incident response tactics in the Gulf Region.

Yealink has thanked Positive Technologies for discovering the critical vulnerability BDU:2024-00482 in its Yealink Meeting Server videoconferencing system.

In an era dominated by digital interactions, Data Privacy Day serves as a stark reminder of the vital need to …

Cloudflare has announced its 2023 Q4 DDoS report – which showed that DDoS attacks reached new heights in 2023. This …

Sophos Positioned as Leader in the 2023 Gartner Magic Quadrant for Endpoint Protection Platforms for the 14th Consecutive Time.

Google Cloud has released its annual Cybersecurity Forecast report for 2024, compiling forward-looking thoughts from security leaders and experts from …

Vectra AI, Inc., the leader in hybrid attack detection, investigation and response, has announced the release of its annual threat …

Qualys, Inc (NASDAQ: QLYS), has released new research from the Qualys Threat Research Unit (TRU), delving into some of the critical vulnerabilities …

Toni El Inati – RVP Sales META & CEE at Barracuda Networks, argues that VPNs have had their day and …