Kaspersky has exposed a new phishing campaign targeting small and medium-sized businesses. The attack leverages the email service provider SendGrid …


Kaspersky has exposed a new phishing campaign targeting small and medium-sized businesses. The attack leverages the email service provider SendGrid …

Edwin Weijdema, Field CTO & Lead Cybersecurity Technologist at Veeam Software, discusses how cyber insurance has become an increasingly popular …

Human-centric threats continue to impact organisations in the UAE, with reports of direct financial penalties due to phishing up 44% and reports of reputational damage up 300%.

Presented by Sertan Selcuk, from OPSWAT, the discussion titled Zero-Trust Approach to Protecting Critical Environments delved deeply in an analysis of decades of company data and insights.

AI-driven SOC Insights analyzes vast amounts of threat and network data to identify what matters most, provides actionable insights, and drives automation with the broader security ecosystem for rapid remediation and containment.

Emad Fahmy is currently the Systems Engineering Manager at NETSCOUT. In this op-ed he discusses how packet data can support the crucial task of protecting digital landscapes from cybersecurity threats.

Ongoing Malicious Campaign Impacting Azure Cloud Environments, Proofpoint Reveals.

After an encouraging decline in 2022, the ransomware landscape saw a major escalation in the frequency, scope, and volume of …

Dave Russell, Vice President, Enterprise Strategy at Veeam explores how zero trust security processes have evolved in recent years and how in a landscape where the benchmark for security is constantly shifting, zero trust must continue to adapt in order to survive.
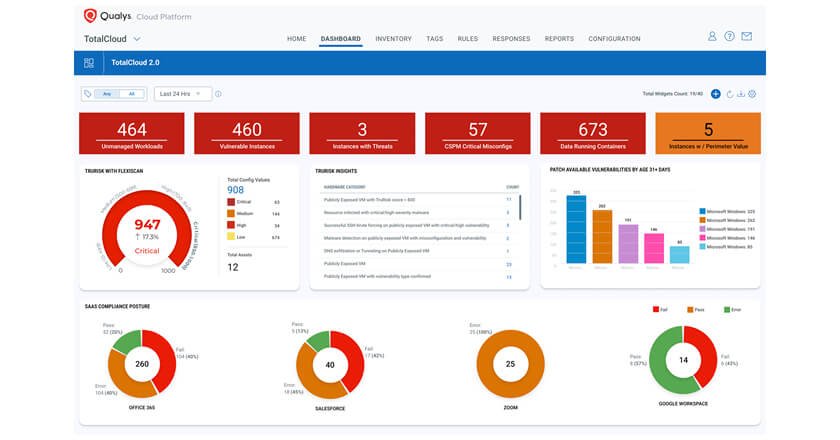
Expanded solution brings cloud infrastructure, SaaS apps and externally exposed assets together for a unified view of risk across multi-cloud environments.

Every day is Safer Internet Day. With data being the soul of businesses as well as virtual and vulnerable, it …
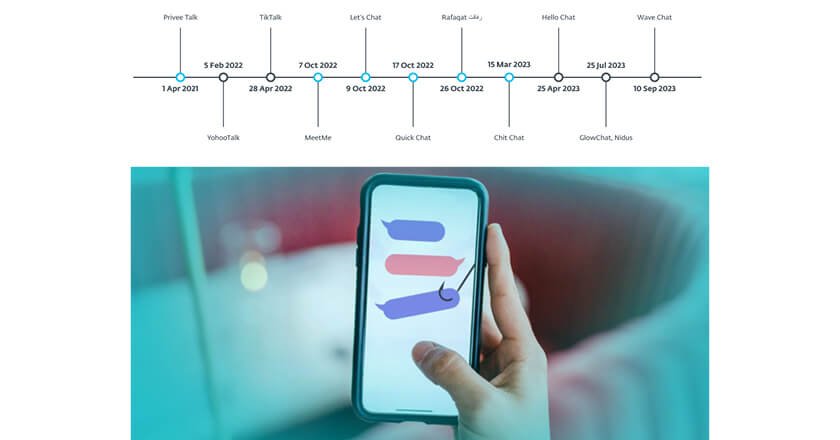
The campaign leveraged Google Play to distribute six malicious apps bundled with VajraSpy RAT code; six more were distributed in the wild.

Expert instructors from SANS Institute will host specialized training in ICS security, as well as the latest threat hunting and incident response tactics in the Gulf Region.

Championing Privacy-First Security: Harmonizing Privacy and Security Compliance.
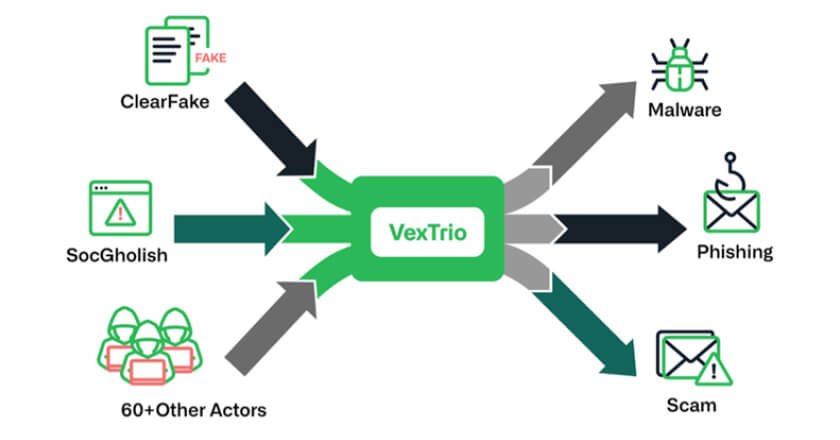
VexTrio has surpassed its counterparts, emerging as the single most pervasive threat in customers’ networks.

Trellix, the cybersecurity company delivering the future of extended detection and response (XDR), has announced Trellix XDR Platform for Ransomware Detection …

Mohamad Rizk, Regional Director, Middle East & CIS at Veeam Software, has penned his technology predictions for 2024, and has …

In 2024, the telecommunications industry will continue to focus on technologies such as cloud computing, standalone 5G, AI, and the Internet of Things (IoT) to offer better speed, scalability, and innovation.

Edwin Weijdema, Field CTO EMEA and Lead Cybersecurity Technologist at Veeam, has penned an exclusive op-ed for tahawultech.com, in which …

Qualys, Inc (NASDAQ: QLYS), has released new research from the Qualys Threat Research Unit (TRU), delving into some of the critical vulnerabilities …