More than half (53%) feel unprepared to cope with a targeted attack, up from 47% the previous year.


More than half (53%) feel unprepared to cope with a targeted attack, up from 47% the previous year.

Ransomware attacks are on the rise, becoming not only more frequent but also more destructive. Rick Vanover, Senior Director, Product …

In today’s digital age, re-evaluating networks and cybersecurity operations is essential, particularly in the UAE, where the threat landscape is rapidly evolving.

Positive Technologies: four out of five attacks targeted in nature.
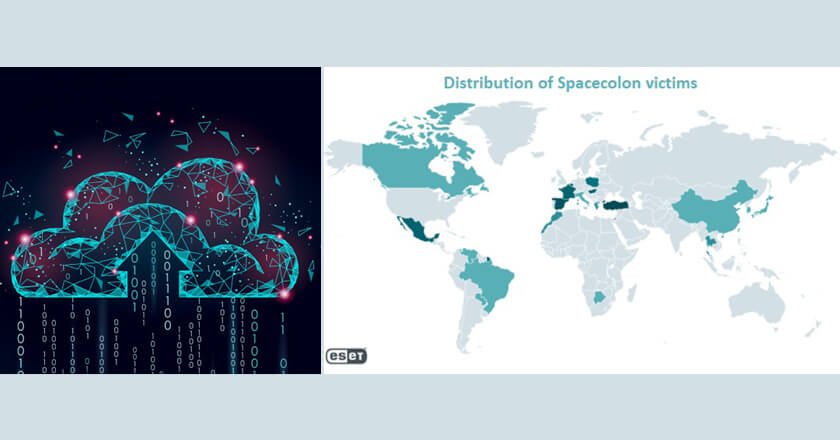
Spacecolon is a small toolset used to deploy variants of Scarab ransomware to victims all over the world, and ESET Research believes it is of Turkish origin.

OPSWAT’s 2023 Threat Intelligence survey highlights the urgent need for enhanced detection capabilities to combat evolving malware threats.
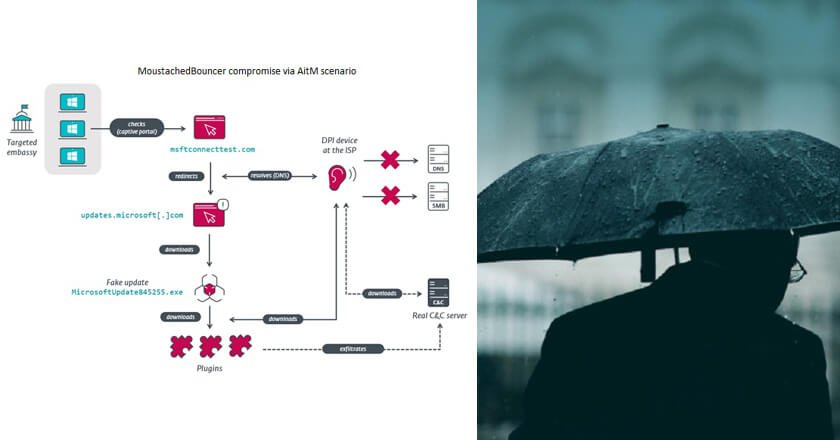
MoustachedBouncer is a threat group, recently discovered by ESET researchers, which specialises in the espionage of foreign embassies, including European ones, in Belarus. It is very likely aligned with Belarus interests.

Trellix Advanced Research Centre’s investigation exposes serious vulnerabilities in CyberPower’s DCIM platform and Dataprobe’s iBoot PDU, highlighting potential unauthorized access …

To stay competitive, it’s essential for organisations to adopt AI technology while safeguarding against potential risks. By taking these steps now, companies can ensure they’re able to reap the full benefits of AI while minimising exposure.
Proofpoint researchers identified a new malware call WikiLoader. It was first identified in December 2022 being delivered by TA544, an actor that typically uses Ursnif malware to target organisations.

Cybercrimes and information security breaches discriminate no one, and the healthcare sector is no exception. With enhanced data storage of …
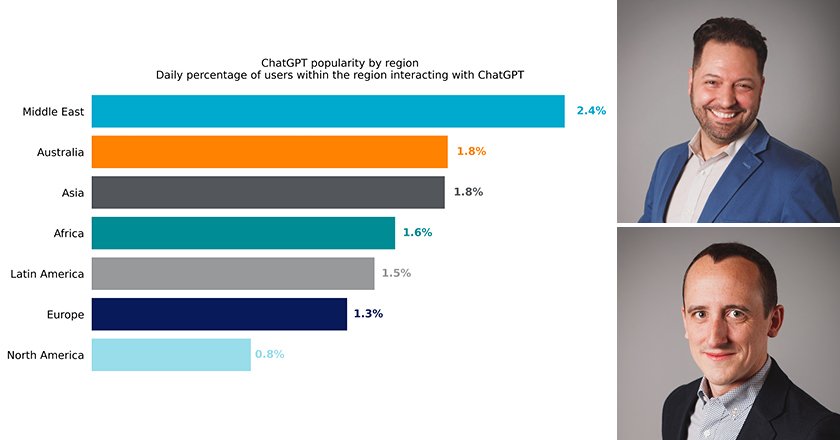
Within the average large enterprise, sensitive data is being shared to generative AI apps every hour of the working day.

This spike reflects a similar trend in the Middle East region, which projected a two-fold hike (103%) in Rootkit detections, as compared to the first five months of last year.

Fady Younes, Cybersecurity Director, EMEA Service Providers and MEA, Cisco has penned a thought-leadership article that provides businesses and employees …

Attacks on Middle Eastern government agencies are mainly carried out by APT groups (56%), covertly establishing themselves in the victim’s infrastructure for the purpose of cyberespionage.
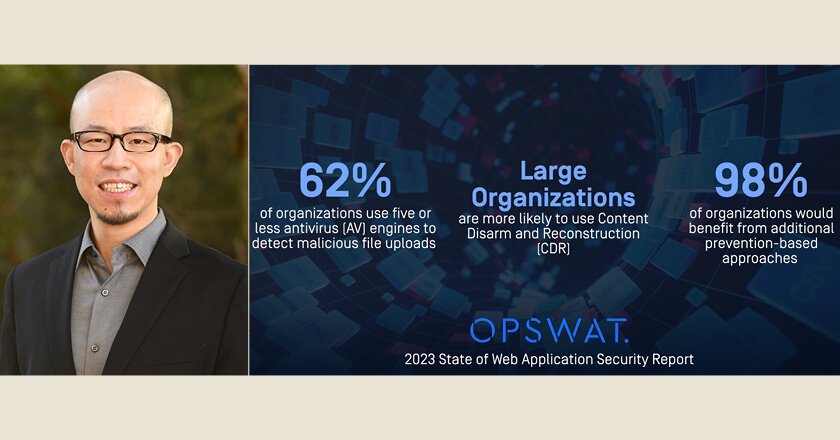
With at least 75% of Organisations Upgrading Infrastructure and 78% Increasing Security Budgets, OPSWAT’s Latest Report Highlights Disparity Between Infrastructure Upgrades, Spending and Security Improvements.

Behavioural correlation of events from multiple sources helps to act faster, get more attack context and start looking for previously unseen activities.

Vibin Shaju, VP Solutions Engineering EMEA at Trellix, explains how XDR is crucial for cybersecurity in GCC as organizations seek …

Ransomware is the only form of cryptocurrency-related crime that has grown in 2023, with attackers on pace for their second-biggest year ever.

Kaspersky unveils a comprehensive report highlighting the increasing peril faced by small and medium-sized businesses (SMBs) in the current cyberthreat landscape.