Sophos’ Annual State of Ransomware report details extensive findings.


Sophos’ Annual State of Ransomware report details extensive findings.

Browser extensions have become an attractive target for hackers looking to exploit unsuspecting crypto users.

Dario Betti, CEO of Mobile Ecosystem Forum, believes that the time has now come for the major stakeholders across the …

Kaspersky researchers announced the discovery of a series of attacks by a new malware supposedly developed by the infamous OilRig …

Tenable credits market share growth to its platform approach to exposure management.

The company also observed two new and significant trends, the use of zero-day vulnerabilities and the exploitation of recently discovered vulnerabilities.

Largest Exposure Management and Vulnerability Management technology partner ecosystem expands program support to include Tenable OT Security.

This Russian-speaking actor uses a wide variety of malware implants developed at a rapid pace and in all programming languages imaginable, presumably in order to obstruct attribution.

The results of the M-Trends 2023 report by Mandiant Inc., now a part of Google Cloud, have been announced and …

Increased deployment flexibility makes exposure management more accessible for customers.

The Most Common Root Causes of Attacks Were Unpatched Vulnerabilities and Compromised Credentials, While Ransomware Continues to Be the Most Common “End Game”.

With 60% of organisations taking more than four days to resolve cybersecurity issues, Unit 42’s Global Incident Response Service dramatically reduces time to remediate threats.

Over 56% of the core routers ESET purchased from secondary market vendors contained a treasure trove of sensitive data, including corporate credentials, VPN details, cryptographic keys, and more.
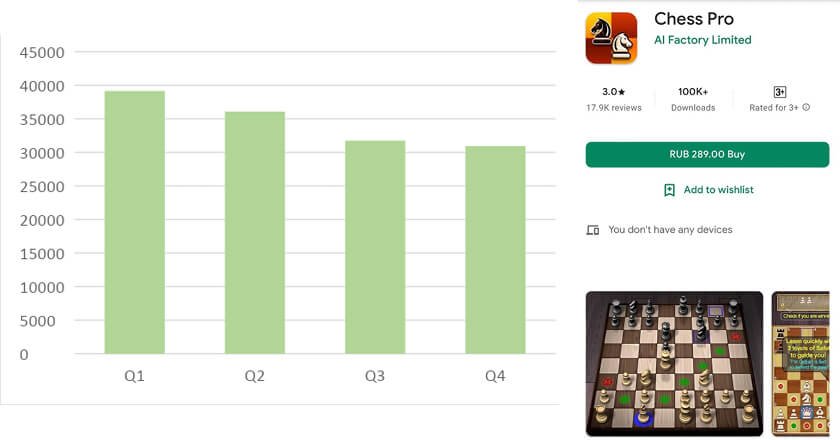
Kaspersky cybersecurity experts have discovered that chess players have been targeted by a range of different attacks from cybercriminals spreading malicious or unwanted mobile programs 一 even on Google Play 一 and Trojans and ransomware disguised as chess applications.

New innovations give teams the ability to deliver sub-second websites with integrated multi-layer security – all from one holistic platform.
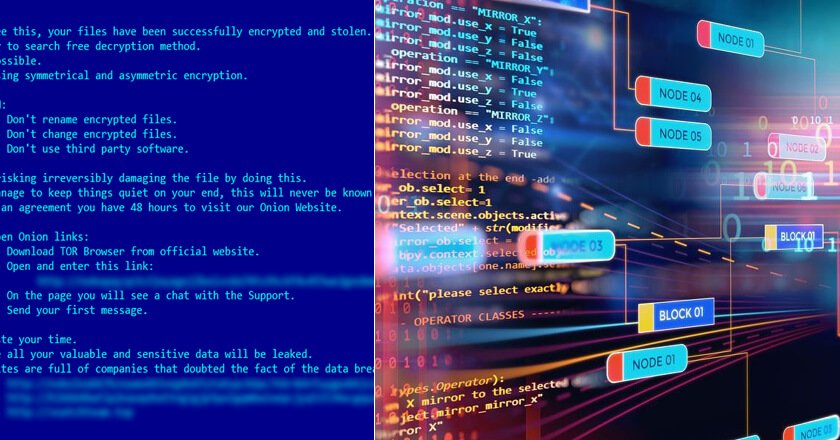
A cybercriminal group used an exploit developed for different versions and builds of Windows OS, including Windows 11, and attempted to deploy the Nokoyawa ransomware.

The event offers high-quality training and insights for cybersecurity professionals in the region, which they can implement immediately to secure their organisations and advance their careers.

Saeed Ahmad, Managing Director Middle East and North Africa at Callsign, outlines what the metaverse means for our digital identities …

As the Middle East makes a concerted effort to grow its knowledge and skills-based economy, the role of data in driving innovation, transformation and success cannot be overstated.

Anoop Das, Enterprise Manager, Middle East at Mimecast tells Anita Joseph all about the company’s channel strategy, technology investments and …