A Philips information management system, which is used in making administrative chores in hospital more efficient, contains vulnerabilities that can …


A Philips information management system, which is used in making administrative chores in hospital more efficient, contains vulnerabilities that can …

Researchers from a Poland-based vulnerability research firm on Friday announced that they had found vulnerabilities in Java 7 Update 11 …

HP TippingPoint, the long-time organiser of the annual Pwn2Own hacking contest, announced on Friday that it will offer cash awards …

A reported vulnerability in Linksys firmware that would allow a hacker to gain full control of the wireless router has …

Oracle’s bad Java week got worse on Wednesday, after it was announced that a previously unknown flaw in the programming …
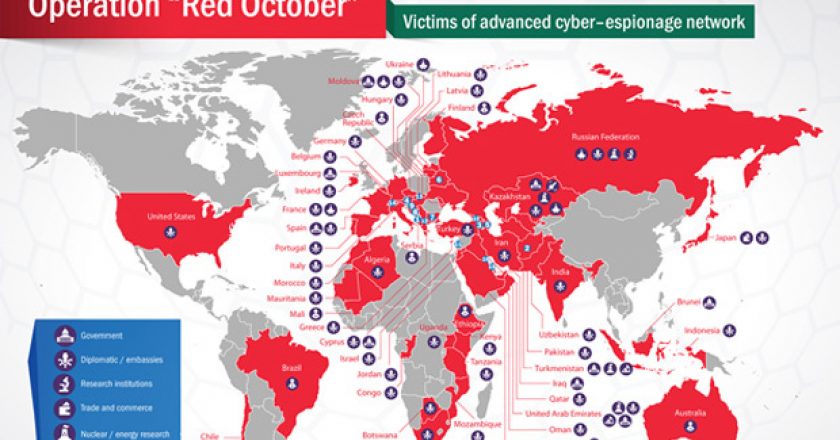
A cyber espionage network has been allowed to flourish in Eastern Europe, former Soviet republics and Central Asian countries since …

Microsoft will deviate from its regular Internet Explorer repair schedule today by releasing a patch for older versions of its …
Following Google’s recent upgrade of Chrome, a new wave of bogus updates has been set upon the Internet by cyber …

Though U.S. officials have consistently blamed Iran for the ongoing stream of distributed denial of service attacks (DDoS) against major …

Security researchers say a patch released by Yahoo earlier this week for a serious email vulnerability did not fix the …

Organisations that adopt Big Data in 2013 will create value and competitive differentiation, while those which do not will stagnate. …

A Chinese man has pleaded guilty in a U.S. court to selling pirated software used in defence, space and other …
A hacker claims to have found a method of bypassing the code integrity mechanism in Windows RT, therefore allowing for …

Cisco Systems plans to release a new patch for a vulnerability in its VoIP phones after the first patch did …

Java 6 will be retired from security support in less than two months, and users and businesses should prepare now …

Adobe plans in February to close a dangerous hole in its Shockwave application that causes the application to be downgraded …

Samsung said Wednesday it is working on an update for a software flaw that could allow attackers to siphon personal …

Trend Micro has updated its mobile security software to detect potential attacks on several Samsung Electronics devices that have a …

If you’re a user of Google’s mobile operating system Android and concerned about your smartphone’s security, expect to worry more …

A hacker in Egypt has released vague details of three vulnerabilities he claims to have found within Yahoo’s website, the …