 A cyber espionage network has been allowed to flourish in Eastern Europe, former Soviet republics and Central Asian countries since 2007, security firm Kaspersky Lab reported this week.
A cyber espionage network has been allowed to flourish in Eastern Europe, former Soviet republics and Central Asian countries since 2007, security firm Kaspersky Lab reported this week.
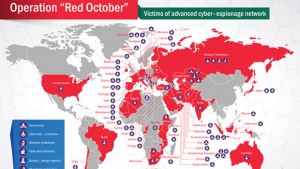
The group, called Red October, has been stealing confidential data from private industry and government and research organisations, the report said.
The network has also stolen sensitive information from organisations in Western Europe and the U.S., but the focus was in the other regions, according to Kaspersky.
Most victims were diplomatic and government organisations, scientific research institutions, nuclear and energy groups, private trade groups and companies in the aerospace industries.
Kaspersky said that it did not know whether the operation was state-sponsored or a criminal group gathering information to sell to the highest bidder. “The most probable scenario is for the end-customer to be a nation-state,” Roel Schouwenberg, Senior Researcher, Kaspersky Lab, said.
The firm discovered the network last year during an investigation stemming from a series of attacks against the computer networks of diplomatic service agencies.
The attackers, believed to have “Russian-speaking origins,” used malware with a unique modular architecture comprising of malicious extensions, information-stealing code and backdoor Trojans. The malware is called Rocra, which is short for Red October.
The cyber espionage network compromised systems of hundreds of victims across 69 companies, Schouwenberg said. “It’s likely there are more victims out there that we’re currently not aware of.”
Like cascading dominoes, computer systems fell as information stolen from one was used to penetrate another. For example, stolen credentials were compiled in a list and then used to guess passwords or phrases to gain access to additional systems.
The attackers created more than 60 domain names and several server-hosting locations in different countries, with the majority in Germany and Russia. The majority of servers were used as proxies, in order to hide the command-and-control server at the core of the operation.
The stolen data had a wide variety of extensions. One extension not seen as a target before was “acid”, which appears to be documents encrypted with classified software called Acid Cryptofiler. The European Union and the North Atlantic Treaty Organisation use the software.
“Previously targeted attacks that have been analysed and reported did not focus on stealing files that were encrypted with Acid Cryptofiler,” Schouwenberg said.
The attackers used spear-phishing emails to lure victims into opening attachments that exploited vulnerabilities in Microsoft Office and Excel applications.
The exploit code had been used before in cyber attacks on Tibetan activists and military and energy-related targets in Asia, Kaspersky said. The embedded executable was unique to Rocra.
Among the unusual attributes of the Rocra malware was a “resurrection” module embedded as a plug-in in Adobe Reader and Microsoft Office applications. The plug-in made it possible for attackers to regain control of a system after the main body of the malware was discovered and removed.
In addition, the malware was capable of stealing data from mobile devices, as well as PCs. Smartphone targets included the iPhone, Nokia devices and phones running Windows Mobile.
Kaspersky conducted the investigation in collaboration with international law enforcement agencies and the Computer Emergency Response Team in Romania and Belarus.
According to the latest report from the U.S. Defence Security Service, cyber-espionage technology is more sophisticated than ever and its use against U.S. targets is growing. From 2010 to 2011, reports of attempts to steal sensitive or classified information and technology rose by 75%.





