Kaspersky Lab experts have uncovered a new cyberespionage campaign “Operation Parliament” that is targeting high profile organisations from around the world with a focus on the Middle East and North Africa.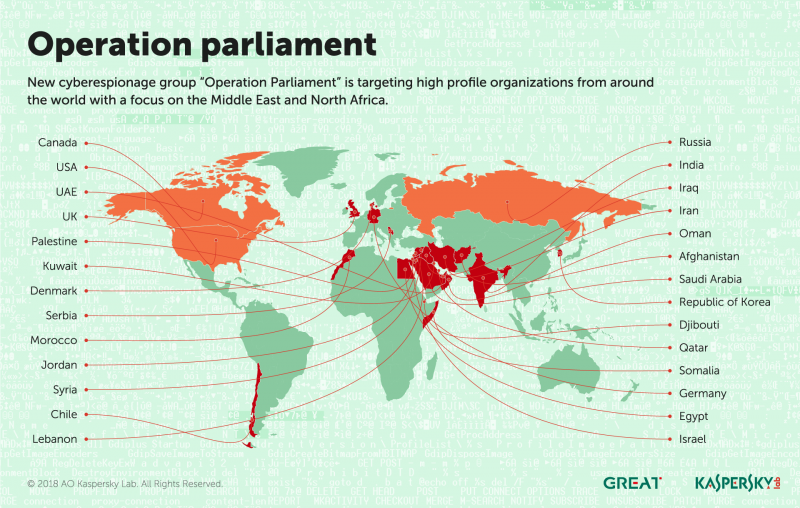
According to the cybersecurity firm, the attacks have been active since 2017 and have targeted top legislative, executive and judicial powers, including but not limited to governmental and large private entities from the region, including the UAE, Saudi Arabia, Jordan, Palestine, Egypt, Kuwait, Qatar, Iraq, Lebanon, Oman, Djibouti and Somalia.
Kaspersky Lab experts believe that “Operation Parliament” represents a new geopolitically motivated threat actor that is highly active and skilled. Attackers are also believed to have access to an elaborate database of contacts for sensitive organisations and personnel worldwide, especially of non-trained staff. Victims of the attacks include government entities, political figures, military and intelligence agencies, media outlets, research centers, Olympic foundations and large private companies.
Based on the findings, the attackers infiltrated their victims using malware that provides them with a remote cmd/powershell terminal that enables them to execute any scripts/commands and receive the result through http requests. The attacks have taken great care to stay under the radar and have used techniques to verify victims’ devices before infiltrating them. Kaspersky Lab products successfully detect and block attacks conducted using these techniques.
“Operation Parliament is another symptom of the continuously developing tensions in the Middle East and North Africa. We are witnessing higher sophistication and smarter techniques used by attackers and it doesn’t look like they will stop or slow down anytime soon,” said Amin Hasbini, Senior Security Researcher at Kaspersky Lab. “The type of people and organisations targeted in this attack campaign should elevate their levels of cyber maturity in order to mitigate such attacks in the future” he added.
In order to prevent falling victim to such an attack, Kaspersky Lab researchers advises organisations to exert special attention and extra measures.
The company highlighted that it is crucial to train staff to be able to distinguish spearphishing emails or a phishing link from legitimate emails and links; use not only proven corporate-grade endpoint security solution but also a combination of specialised protection against advanced threats, such as Threat Management and Defense Solution, which is capable of catching attacks by analysing network anomalies; and follow strict rules to avoid data leaks and deploy techniques to prevent insider threats.





