Ocado, an online-only grocery retailer, has recently developed a 4G-based protocol to communicate with thousands of robots powering its new automated warehouses.


Ocado, an online-only grocery retailer, has recently developed a 4G-based protocol to communicate with thousands of robots powering its new automated warehouses.

UAE-based satellite operator Yahsat has recently announced that it entered into a strategic partnership with Talia, a teleport, satellite and terrestrial network operator.

Cisco has announced their participation in the 4th E-Government Forum (EGOV4) in Kuwait, which will be held from 27th to 29th November at Courtyard Marriott hotel.

Amazon.com Inc is said to be in discussions with Souq.com over a $1 billion purchase of the Dubai-based online retailer.

James Lyne, Global Head of Security Research, Sophos, shares a Black Friday security checklist of top 10 consumer traits that leave them vulnerable to cybercriminals.

International Data Corporation (IDC) has recently hosted its inaugural UAE Banking and Finance Congress at the Jumeirah Creekside Hotel in Dubai.
TP-Link Technologies has announced that it will be demonstrating its commitment to Egypt’s ICT sector by returning to Cairo ICT 2016.
ASBIS Enterprises has announced that it signed an agreement with Kingston Technology Company for the distribution of the vendor’s complete range of products across the Gulf and North Africa region.

Pure Storage has recently introduced the availability of petabyte-scale storage for mission-critical cloud IT, anchored by the release of the next-generation of FlashArray//m the company’s flagship all-flash storage array.
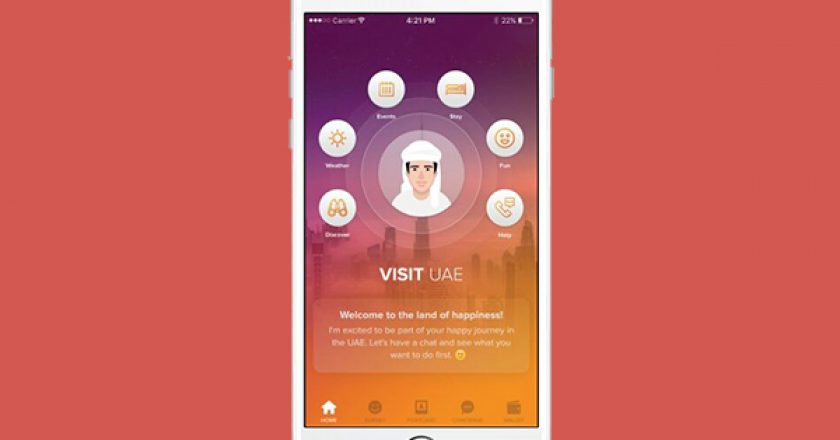
The UAE Ministry of Economy (MoE) has launched the first phase of its ‘Be Happy – Visit UAE’ application as part of its featured initiatives for UAE Innovation Week 2016.