Tenable, recently announced it has been named a ‘Leader’ in the GigaOm Radar for Operational Technology (OT) Security.


Tenable, recently announced it has been named a ‘Leader’ in the GigaOm Radar for Operational Technology (OT) Security.

Christos Tulumba, Chief Information Security Officer at Veritas Technologies, has penned a comprehensive op-ed designed to provide CISO’s with a …

Built on Cisco’s Full-Stack Observability Platform, Cisco Secure Application provides organisations with intelligent business risk insights to help them better prioritise issues, respond in real-time to revenue-impacting security risks and reduce overall organisational risk profiles.

Anita Joseph spoke to Rakesh Ragudharan, Vice President, Strategic Initiatives, Bahwan CyberTek, on how a hybrid security approach blends the …

Industry’s largest repository of threat, vulnerability and asset data enables unprecedented intelligence to quickly identify and mitigate cyber risk.

In today’s digital age, re-evaluating networks and cybersecurity operations is essential, particularly in the UAE, where the threat landscape is rapidly evolving.

Positive Technologies: four out of five attacks targeted in nature.

It Takes Less Than a Day for Attackers to Reach Active Directory—Companies’ Most Critical Asset. The Vast Majority of Ransomware Attacks Occur Outside of Business Hours.

Boeing Recognised as A ‘Hybrid Workforce Innovator’ for Fostering Collaborative Engineering at Global Scale with VMware Anywhere Workspace.

The bottom line is that organisations need an application observability solution which meets the current and future needs of all technologists, enabling them to accelerate innovation and deliver seamless and engaging digital experiences to both the organisation and external customers.

Taj El-khayat, Area VP, South EMEA, Vectra AI reveals GCC’s $7.45M ransomware impact overshadows global averages, fueling demand for AI-powered …
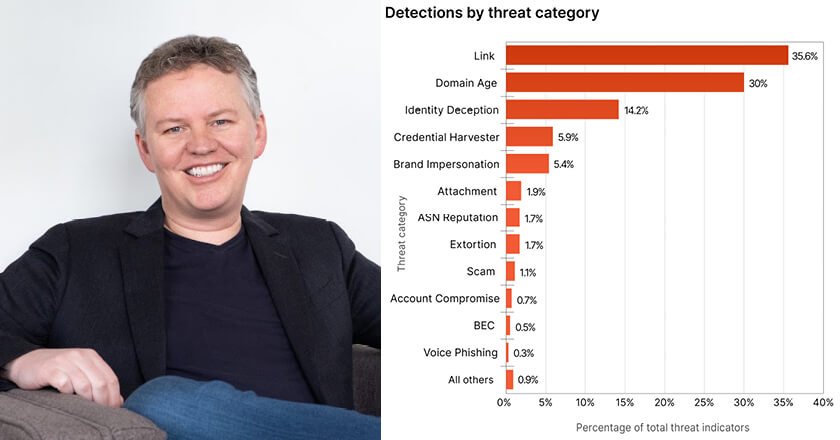
Report underscores that email is the most exploited threat vector, phishing remains borderless and attackers are increasingly impersonating trusted name brands.

Trellix Advanced Research Centre’s investigation exposes serious vulnerabilities in CyberPower’s DCIM platform and Dataprobe’s iBoot PDU, highlighting potential unauthorized access …

Industry’s largest repository of threat, vulnerability and asset data enables unprecedented intelligence to quickly identify and mitigate cyber risk.

Layale Hachem, senior solutions engineer at BeyondTrust explains how businesses can defend against IABs by enforcing least privilege, enhancing multi-factor …
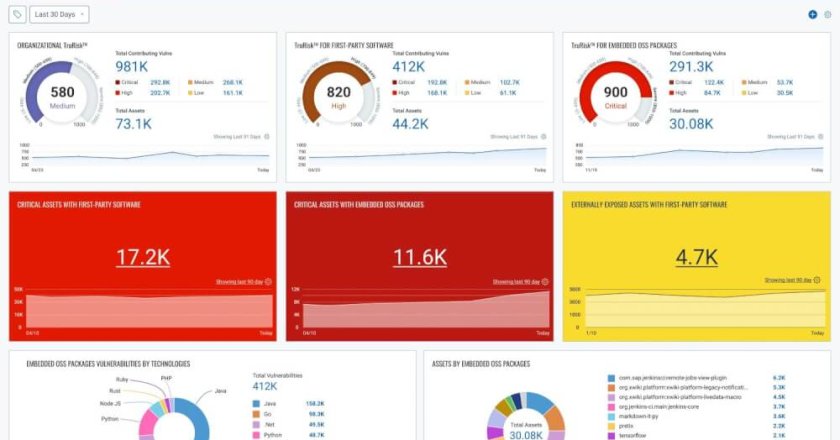
Qualys, Inc. (NASDAQ: QLYS) launches a game-changing solution enabling AppSec teams to personalize risk assessment and remediation for their proprietary …

New Cloud Native Detection and Response capabilities provide security teams with real-time, unified visibility and context into containers and Kubernetes environments.

Open source web server powering more than 400 million websites enhanced with new enterprise-level capabilities.

With the explosion of digitisation across industries, opportunities for fraud and financial crime have grown exponentially.

Because MFA is a significant improvement over password-only authentication, it is here to stay, so cybersecurity practitioners must address its vulnerabilities.