Before downloading any software, check for digital signatures to ensure that the software is authentic and has not been tampered with.


Before downloading any software, check for digital signatures to ensure that the software is authentic and has not been tampered with.

It happens to all of us — that one precious photo or video that immortalised a special moment but doesn’t …

Cloud service providers now recognise their responsibility for security lies around their infrastructure and services provided for enterprises says Tamer Odeh, Regional Sales Director, from SentinelOne.

A prominent supplier of cloud-based IT, security, and compliance solutions, Qualys Inc. (NASDAQ: QLYS), has issued its 2023 TruRisk Research …

Veronica Martin caught up with Ashley Beck, Senior Industry Consultant – Global, Fraud & Security Intelligence Division at SAS, at …

Anita Joseph caught up with Werno Gevers, Regional Manager, Mimecast Middle East to learn more about Business Email Compromise and …

BeyondTrust, a global pioneer in intelligent identity and access security, has released the 2023 Microsoft Vulnerabilities Report. This study is …

Veronica Martin caught up with Maher Yamout, Senior Security Researcher at Kaspersky during GISEC 2023 to discuss the products and …

This Agreement will Aim to easily enhance enterprises security posture with Yogosha’s unique Vulnerability Operations Centre (VOC).

By Q3 2022, the proportion of phishing attacks had risen by 1.3 times, representing 76 percent of all attacks, up from 58 percent in Q1.

Moreno Ciboldi –SVP Channels & Alliances, Teksalah, on what to look forward to at GISEC, the products and solutions it is showcasing at the event, and cyber resilience-the theme for this year.

Nearly 60% of companies in UAE and Saudi Arabia need to increase cybersecurity spending, reveals Mimecast report.

Satykam Acharya, Director Red Team, Infopercept Consulting Pvt Ltd on offensive security and why it is important today. English grammar …

Kaspersky’s latest report ‘The Dark Side of Kids’ Virtual Gaming Worlds explores the risks for young players in online gaming and analyses threats related to the most popular online games for 3-16-year-old kids.

2022 Threat Landscape Report reveals that the most commonly exploited vulnerabilities were up to five years old.

Product Enhancements Offer Increased Data Protection and Mitigate Increasingly More Sophisticated Threats.

Latest Cyberthreat Trends Detailed in Trellix Advanced Research Centre Report.

“If anyone on a dating app is trying to get you to invest money into something, it’s a huge red flag”.

Cyber Immunity to be a key IT security theme across META region in 2023 and beyond.
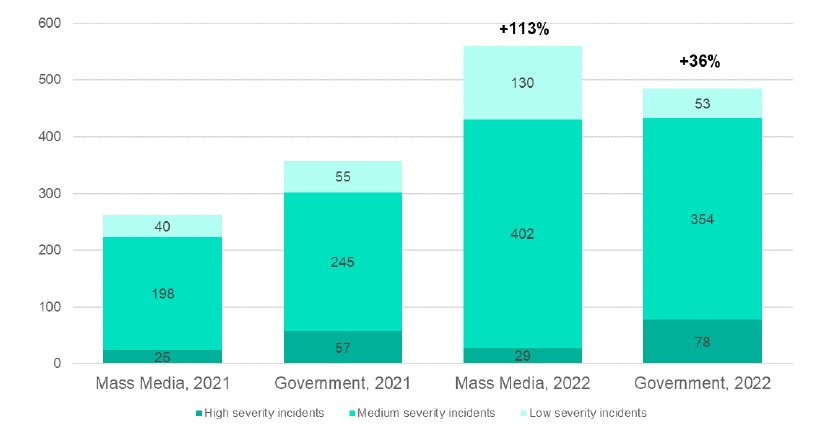
SOCs to face greater challenges from cybercriminals targeting governments and media.