A KPMG study reveals that less than ten percent of businesses believe they are in a position to make use of the information they have on customer preferences, behaviour and demands.


A KPMG study reveals that less than ten percent of businesses believe they are in a position to make use of the information they have on customer preferences, behaviour and demands.

With security so high on the agenda, businesses are doing everything they can to safeguard their networks from cyber-criminals keen to capitalise on software exploits. But do businesses pay enough attention to software updates when there are hundreds of other issues to address?
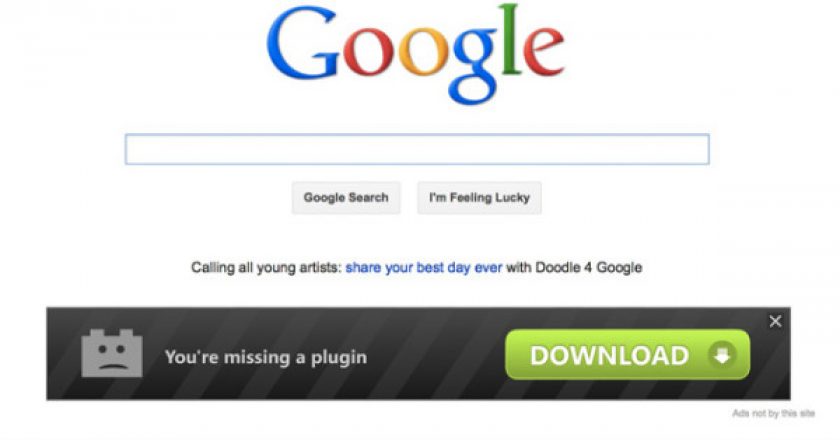
Changes in Google Chrome extension ownership can expose thousands of users to aggressive advertising and possibly other threats, two extension developers have recently discovered.

With Windows 8 bearing a good share of the blame for the declining PC market, HP is falling back on Windows 7 for its latest marketing push.

Seventy percent of CIOs plan to change their relationships with technology providers and outsourcing partners over the next two to three years, according to a Gartner survey.

The world is still in the foothills of the cyberwar era but already online confrontation is being defined by an unstable and possibly dangerous mixture of proxy conflicts and old-fashioned espionage, mixed with lower-level digital activism, security firm FireEye has said.

Digitalisation – the third era of enterprise IT – has begun, but most CIOs do not feel prepared for this next era, according to a global survey of CIOs by Gartner.

Palo Alto Networks has announced enhancements to its enterprise security platform WildFire.

Oracle is about to release one of its largest security patch batches in recent memory, with some 147 fixes coming Tuesday for vulnerabilities in Java SE, its flagship database, business applications and assorted other products.

A deeper look by Cisco Systems into the cyberattack that infected Yahoo users with malware appears to show a link between the attack and a suspicious affiliate traffic-pushing scheme with roots in Ukraine.

The world’s largest networking vendors have hit back at claims their products have been compromised by the National Security Agency after being named in an NSA spying toolkit.

Today’s information security professionals need to learn more swiftly, communicate more effectively, know more about the business, and match the capabilities of an ever-improving set of adversaries.

Worldwide IT spending is projected to total $3.8 trillion in 2014, a 3.1 percent increase from 2013 spending of $3.7 trillion, according to the latest forecast by Gartner.

A team of malware developers is preparing to sell a new ransomware programme that encrypts files on infected computers, according to a volunteer group of security researchers who tracked the development of the threat on underground forums in recent weeks.
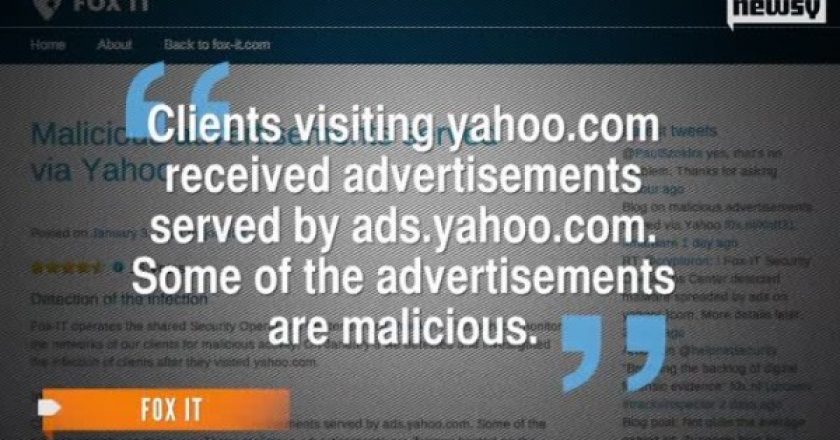
Yahoo said that malware spread by advertisements served by its European websites had not affected users in North America, Asia Pacific and Latin America as people in these locations did not receive them.

Symantec has warned against remote access Trojans, programmes that are installed on a user’s computer without their knowledge and allow attackers to access and control them from remote locations.

Phone numbers paired with user names of over 4.6 million alleged Snapchat users were posted online by hackers, a few days after a security research group claimed a vulnerability in the social sharing service that could allow attackers to match phone numbers to Snapchat accounts.

A Russian hacker gained access to a BBC server over the Christmas period and attempted to sell access to it to other cybercriminals, reports suggest.

Through the partnership, the distributor will deliver Venafi products and solutions for Middle East, Turkey and Africa customers through its channel partners.

Major technology developments over the last year—and a series of revelations about the National Security Agency that shook the international security community—made 2013 an interesting year. In highlighting the past year’s security events, we’ve considered some emerging trends we are likely to see in the coming year.