The overall global Internet threat level grew by 6.9 percentage points in 2013, with 41.6 percent of user computers being attacked at least once, according to Kaspersky Lab.


The overall global Internet threat level grew by 6.9 percentage points in 2013, with 41.6 percent of user computers being attacked at least once, according to Kaspersky Lab.

The potential business impact of cyber attacks and data loss, along with high-profile data breaches experienced by organisations like LexisNexis andEvernote, seems to have done little to convince small and mid-size businesses that they should be making cyber security a priority.

Reading the coverage of the recent breach of Adobe passwords, we learned that 1.9 million users used “123456” as their password. That’s right: out of 38 million cracked passwords, almost two million adults used ones more suited to five-year-olds.
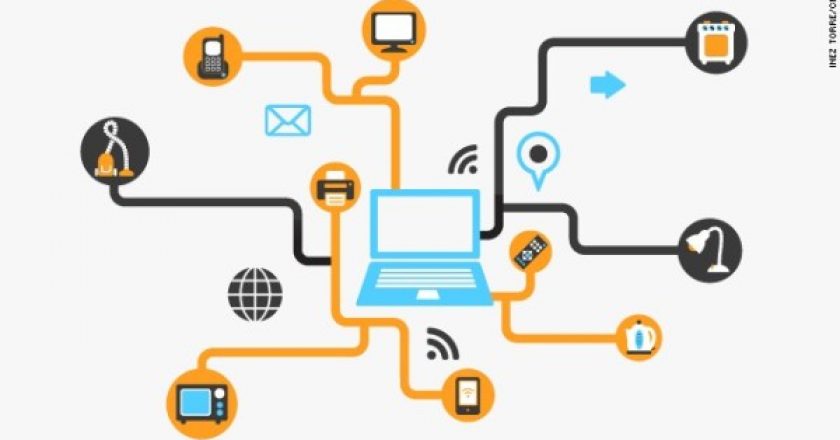
The Internet of Things, which excludes PCs, tablets and smartphones, will grow to 26 billion units installed in 2020 representing an almost 30-fold increase from 0.9 billion in 2009, according to Gartner.

New attack campaigns have infected point-of-sale (PoS) systems around the world with sophisticated malware designed to steal payment card and transaction data.

On any given day cybercriminals and nation states are in possession of as many as 100 zero-day software exploits known only to them, NSS Labs has calculated using the commercial vulnerability market as a baseline.

Thirteen people, including the creator of Blackhole, a popular exploit tool used to infect computers with malware, were arrested and charged in Russia with creating and participating in a criminal organisation.

Security researches at Symantec are gradually raising warnings that the Internet of Things will increase, by multitudes, the number of things that can be hacked and attacked.

Balancing security priorities with business flexibility and agility is a tough challenge, says Anthony Perridge, EMEA Channel Director, Sourcefire.

IT departments are “significantly underestimating” the budgets allocated to technology in others parts of the organisation, as more business leaders bypass the CIO and IT staff to execute their own projects, according to research.

A new Trojan programme that targets users of online financial services has the potential to spread very quickly over the next few months, security researchers warn.

The most successful businesses use DevOps to remove any roadblocks that stand in their path, writes Alan Hale, director of EMEA Consulting at Red Hat.

A manufacturer of glass coverings for Apple is drawing accusations of worker exploitation from Hong Kong labour groups concerned with several employee suicides at its factory in China.

Cybercriminals are increasingly using the “Blackshades” malware program whose source code was leaked three years ago, according to an analysis by Symantec.

The U.S. National Security Agency reportedly hacked into over 50,000 computer networks around the world as part of its global intelligence gathering efforts, and also taps into large fiber optic cables that transport Internet traffic between continents at 20 different major points.

The website of a U.S. organization specializing in national and international security policy was compromised with malware that targeted a previously unknown vulnerability in Internet Explorer.

Security researchers have uncovered two unpatched vulnerabilities in Internet Explorer (IE) which have been exploited by attackers in an unusual “watering hole” campaign launched from a U.S.-based website that specialises in domestic and international security policy.

The federal deficit – the amount by which the US government’s total budget outlay exceeds its total receipts for a fiscal year – is estimated at $680 billion for 2013.
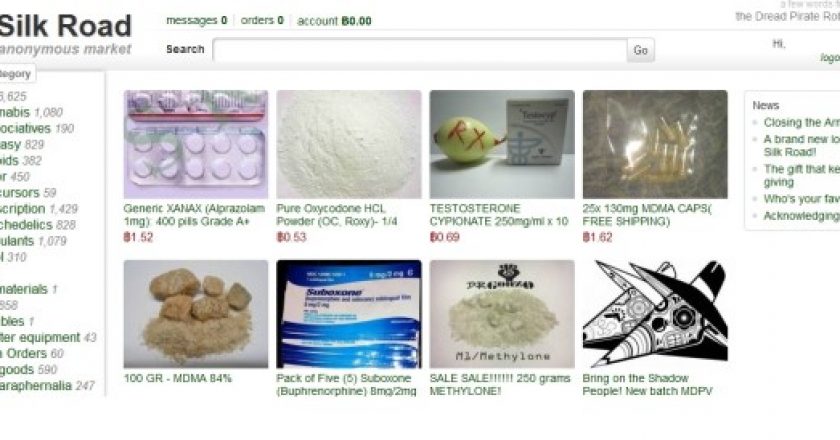
The Silk Road online marketplace has resurfaced about a month after U.S. officials shut down the website that was only accessible through the Tor anonymity service.

Spear phishing is one of the most effective ways to break into a corporate network – and recent studies show that employees can be easily tricked on social media to provide the information needed to launch attacks.