
In recent years, cyber-attacks have become a major concern for all customers due to the wide variety of approaches and subversive nature. Malware and ransomware attack cases are doubling year over year according to leading industry analysts, with millions of malware infections and thousands of ransomware attacks per day (Source: Symantec 2018 Internet Security Threat Report, Panda Research, PWC, Juniper Research). For mission-critical databases, such attacks leading to lost data and system downtime can have far ranging impacts throughout the business in terms of revenue, operations, reputation, and even penalties.
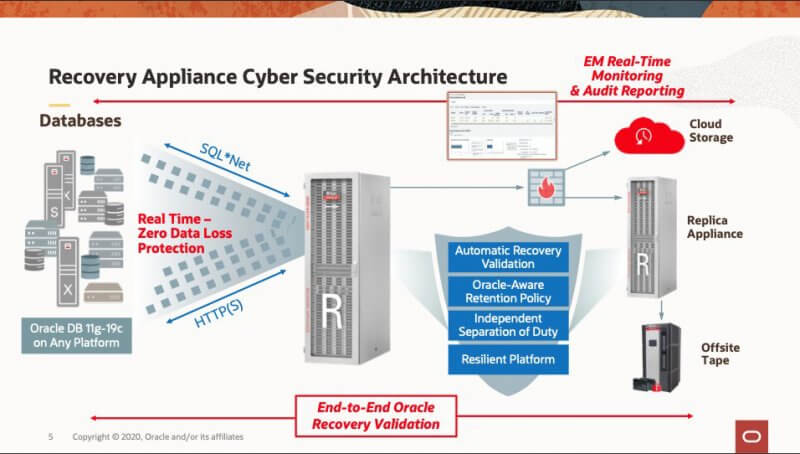
As the premiere Oracle Engineered System for database protection, Zero Data Loss Recovery Appliance is fault-isolated from the production database, so if a cyber-attack hits the database, the appliance is not compromised. This is due to the following key architectural features:
End-to-end recovery validation and retention management
While validation is key to detecting corrupt backup data throughout the backup lifecycle, it is equally important for detecting cyber-attacked data. Since the appliance validates all incoming, on-disk, and replicated backups for Oracle block correctness and recoverability, any backup data maligned by malware or ransomware attack will be detected, recorded, and alerted to the administrator. Action can then be taken in conjunction with the DBAs to disconnect the database from the network and investigate further. Furthermore, replicated backups cannot be deleted or modified by the primary appliance or its administrators – they are independently validated and managed by the replica appliance, thus shielded from any effects of attacks done on the primary appliance.
Each appliance operates independently with respect to its configured Oracle-aware retention policies, so that backups required for database recovery within the stated retention period are always available. Backups not needed are automatically purged. This is all managed by the appliance, without having to run separate RMAN validate or delete operations.
As an alternative or supplementary protection strategy, backups can be archived from the appliance to Oracle Cloud Storage, a secure, offsite location, using Oracle Key Vault as key store for the archived backup encryption keys – all backups are validated and encrypted prior to being sent to Cloud Storage and users require access to the Recovery Appliance and Oracle Key Vault to perform restore operations. Backups can also be archived to fiber-attached tape libraries using the bundled Oracle Secure Backup media management software – tapes can then be shipped to and stored in a network-disconnected, offsite location that is impervious to cyber-attacks.
Separation of duty
Access to the system is controlled via strict separation of duty between DBA and appliance administrator roles. DBAs are only given Virtual Private Catalog (VPC) user roles to backup and recover their privileged databases – they cannot access, modify, or delete backups on the appliance. Recovery Appliance administrators only have access to manage and monitor the system, but cannot backup, recover, or modify protected databases. Furthermore, the appliance does not expose or allow creation of local users, databases, or other services.
Limited network access
With regards to network protocols, VPC users can only connect to the appliance via SQL*Net, while HTTP(S) is used for RMAN backup and restore traffic via the Recovery Appliance Backup Module – no other protocols are employed. In addition, the appliance enforces network segregation with the support of VLAN tagged networks, allowing backup and restore traffic to be fully isolated and non-routable between protected databases’ specific network zones – in this way, any possibly affected backups would not be exposed to the rest of the enterprise.
Superior resiliency
The appliance itself offers superior resiliency capabilities against cyber-attacks, when compared with traditional backup appliances. As an Oracle Engineered System built on Exadata hardware and storage, the appliance inherits a resilient architecture for reducing surface of attack on compute and storage servers – this includes hardened password policies, OS and DB user auditing, firewall support, and Oracle ILOM (Integrated Lights Out Management). Refer to the Oracle Exadata Security Guide for more details.
Zero data loss recovery
Finally, in the event that a database server is attacked and its backups must be recovered to a different server, the Recovery Appliance real-time redo transport allows recovery to the very last transaction prior to the attack occurrence. This is especially important for cyber-attacks, such as ransomware, where paying the perpetrators does not always mean your data comes back in pristine condition. With Recovery Appliance, don’t pay the ransom – just recover the database to a separate, safe location with no data loss.
Net-Net
As cyber warfare has grown to become a recognised threat to enterprises, the impact on Oracle databases can especially put businesses at risk, given that the databases typically manage the most critical business data assets for the business. As the premiere Engineered System for Oracle Database protection, the Recovery Appliance inherently provides superior resilience and recovery capabilities against database cyber-attacks. These include end-to-end recovery validation, separation of duty, limited network access, Exadata-based security resiliency, and of course, zero data loss recovery in the event that the production database is hit by an attack.
To find out more about Oracle’s Zero Data Loss Recovery Appliance, click here.





