Group-IB, one of the global leaders in cybersecurity, has today published its research into a wide-scale phishing scheme that sees scammers impersonate one of the leading manpower agencies in the Kingdom of Saudi Arabia (KSA). In total, analysts from the Group-IB Computer Emergency Response Team (CERT-GIB) and Digital Risk Protection Team based at the company’s Threat Intelligence and Research Centre in Dubai, UAE analysed more than 1,000 rogue domains created to impersonate the manpower provider in question as part of a long-term scam campaign.
Group-IB analysts uncovered how one individual claimed to be offering more than 100 domain names that contained a logical connection to, or a variation of, the brand name in question. In line with Group-IB’s zero-tolerance policy towards cybercrime, Group-IB analysts notified the Saudi Computer Emergency Response Team (CERT-SA), a fellow OIC-CERT member, of their findings to assist their regional partners in taking any relevant action to combat this scheme.
A full breakdown of the scheme can be found in a new Group-IB blog post.
Scam in action
In 2021, more than $55 billion was stolen from victims as a result of scams, according to a Global State of Scam Report that Group-IB contributed to. The need to combat scammers is all the more pertinent given that recent Group-IB research found that scams accounted for 57% of all financially motivated cybercrime, and, according to the Global Anti Scam Alliance, the number of scams is growing more than 10% year on year. The same report also revealed that users in Saudi Arabia are targeted by the most phishing scams in the Middle East.
Domain spoofing, known as the faking of a website or email domain to make malicious sites or emails look credible, has long been a tactic of cybercriminals across the globe, and we are seeing new schemes appearing with alarming regularity. This past July, Group-IB uncovered more than 270 domain names that mimicked over a dozen postal and logistics brands across the Middle East in a separate scam campaign.
However, the postage scam scheme identified by Group-IB has been dwarfed in size by a new wide-scale domain and website spoofing campaign targeting users in Saudi Arabia. Over the past 16 months, Group-IB analysts analysed more than 1,000 rogue domains linked to a single Saudi company – a leading manpower agency that offers businesses assistance in hiring employees for the construction and services sector, and individuals can also procure the services of domestic workers through the agency. The latter of these two groups is the target of this scam campaign.
The campaign, which was launched in April 2021, appeared to peak in March 2022, when more than 200 new domains spoofing the agency in question were registered with hosting providers. Group-IB analysts believe that the surge in new domains registered in early 2022 could be a sign that a growing number of internet users had fallen victim to this scheme. As seen in other examples around the world, scammers often double down on a certain tactic once it starts to generate them money.
A full breakdown of the scheme’s timeline can be found below:
In April 2022, when the phishing campaign surged, financial bodies in Saudi Arabia warned of a sharp increase in financial fraud in the country in the preceding year. Group-IB analysts assume that the subsequent reduction in the number of new domains registered per month imitating the manpower provider has followed in the wake of warnings to users by financial authorities in Saudi Arabia, government institutions, and the brand itself. However, the creation of 32 new spoof domains in September 2022 alone shows that scammers are still attempting to impersonate the company.
According to Group-IB’s findings, the driving factor for this scam scheme is an unholy alliance between scammers and spoof domain brokers. This alliance sees the brokers purchase the rights to dozens of domain names containing a typographical or phonetic variation of the attacked brand, and offer them for sale at a low price to scammers.
Imitation – the sincerest form of flattery
The URLs and the design of the scam pages created as part of this campaign are intended to convincingly imitate the manpower provider in question and trick users into entering their credentials for banking services and online government portals. The scammers can harvest both login information and two-factor authentication (2FA) codes to gain access and complete fraudulent transactions.
The scam campaign, which rests on multiple layers of social engineering, starts with the scammers placing advertisements on social media sites such as Facebook and Twitter, and the Google search engine. Group-IB analysts discovered more than 40 individual advertisements for this scheme on Facebook alone.
From there, the victims begin interacting with the scammers via SMS or WhatsApp communication, and a full breakdown of an average victim journey can be found below:
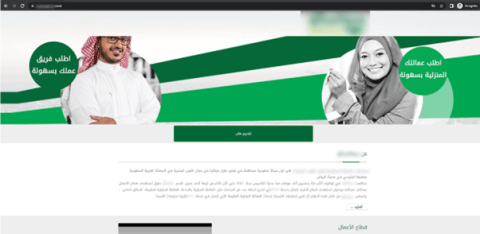
The phishing pages created by the scammers contain the official logo of the targeted brand as a means of building legitimacy in the eyes of the victims.
Upon landing on the homepage of the phishing site, the victim is directed to click the large green button that has “apply” written on it. Once they do this, they are transferred to a second page where they are requested to enter their personal information.
After entering their personal information and clicking “apply”, the victims are redirected to a page that asks them to select the nationality of the domestic worker they wish to hire.
The next stage of the scam sees victims choose the type of domestic service they require (e.g., hourly, in-house).
Once they have completed these steps, the victim is transferred to a page on which they are asked to pay a small processing fee of 50 or 100 SAR (approximately $13 or $27). In fact, this transaction will not take place, as it is merely a ploy for the scammers to harvest credentials, but the victims are presented with the choice of making this fake transaction either via bank payment or a Saudi government portal.
Irrespective of how the victim chooses to make the fake payment, they are sent either to a page emulating 11 regional banks or a website impersonating a Saudi government portal. The likelihood of the victim of being directed to the fake bank page or the fake portal page appeared to be random. In both cases, the victim’s login credentials and two-factor authentication (2FA) code are harvested by the scammers.
Once the victim enters their data, the threat actors harvest the victim’s login credentials and 2FA code, which can be used to gain access to the victim’s bank or governmental portal account and begin making fraudulent transactions until the account is emptied.
Interestingly, the domain names identified by Group-IB in this scam campaign are registered with the same popular and affordable hosting providers as seen in many other phishing schemes. This underlines how fraudsters worldwide are utilising similar tactics, such as launching domains with cheap, easy-to-register, and stable hosting providers, to target victims across the globe.
“The primary goal of this research is to raise public awareness in the Middle East of the latest phishing attacks, and to call for internet users to remain vigilant as threat actors continue to convincingly, and with increased regularity, impersonate some of the region’s largest organisations. Scammers are becoming increasingly resourceful and collaborative, and spoof domain brokers are coming to the assistance of cybercriminals. We encourage companies and organisations to monitor for signs of brand abuse, and we also urge internet users to remain vigilant so that they do not become victims of scams such as this”, Mark Alpatskiy, CERT-GIB Senior Analyst, said.
In order to prevent further phishing attacks using spoof domains, companies and organisations should monitor for signs of brand abuse across the internet, including on social media which is often used by scammers to advertise their phishing pages. Group-IB’s Digital Risk Protection solution helps firms and organisations secure their digital assets by continuously and automatically monitoring millions of online resources where brand or intellectual property may be present.
Internet users are urged to show caution and always check the URL domain of the page they are accessing and verify it to see if it is the official website before entering any personal or payment details. Another recommendation is to maintain communication with online chat services or call centres of the official company or organisation.





