Each scenario demonstrates the cybersecurity’s true role in terms of business continuity and profitability, highlighting emerging challenges and threats.



Each scenario demonstrates the cybersecurity’s true role in terms of business continuity and profitability, highlighting emerging challenges and threats.
A series of malicious actions allow the extension to run stealthily while the user is browsing the internet. As a result, threat actors become capable of transferring the BTC from the victim’s wallet to their wallet using web injections.

Gaurav Mohan, VP, SAARC & Middle East, NETSCOUT explains how depending solely on endpoint detection is not enough to protect …

Steven Kenny, Architect & Engineering Program Manager, and Andrea Monteleone, Segment Development Manager, Critical Infrastructure, at Axis Communications, have joined …

Anita Joseph caught up with Aloysius Cheang, Chief Security Officer at Huawei Middle East and Central Asia, to find out …
Kaspersky experts continuously monitor the mobile threat landscape and track threat trends to provide the most up-to-date intelligence about the potential dangers.

Anita Joseph caught up with Luca Brandi, EMEA Channel Sales Director at Trellix, to learn more about Xtend, the company’s …

BeyondTrust, the worldwide leader in intelligent identity and access security, has announced the addition of new and updated tools, processes, …

Sammy Zoghlami, Senior Vice President EMEA at Nutanix, tells Tahawultech.com all about hybrid cloud adoption and the steps that companies …
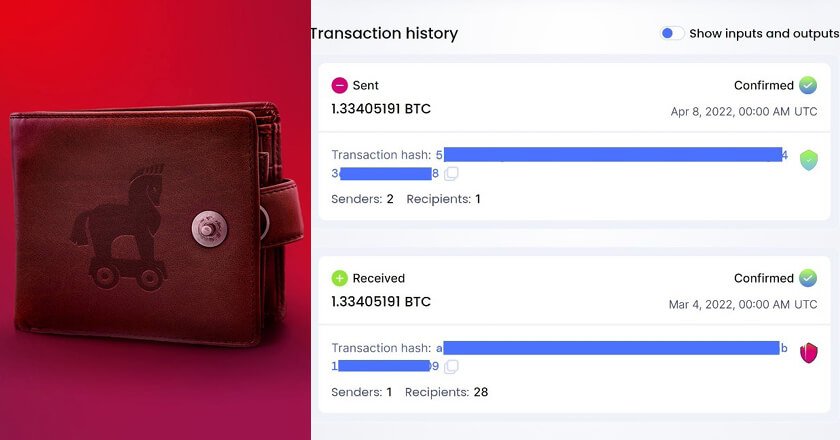
Kaspersky shared the details behind the incident of cryptocurrency theft involving a hardware wallet, which resulted in the loss of 1.33 BTC worth $29,585.