Kaspersky Lab has discovered a new wave of targeted attacks against the industrial and engineering sectors in multiple countries around the world, including the UAE.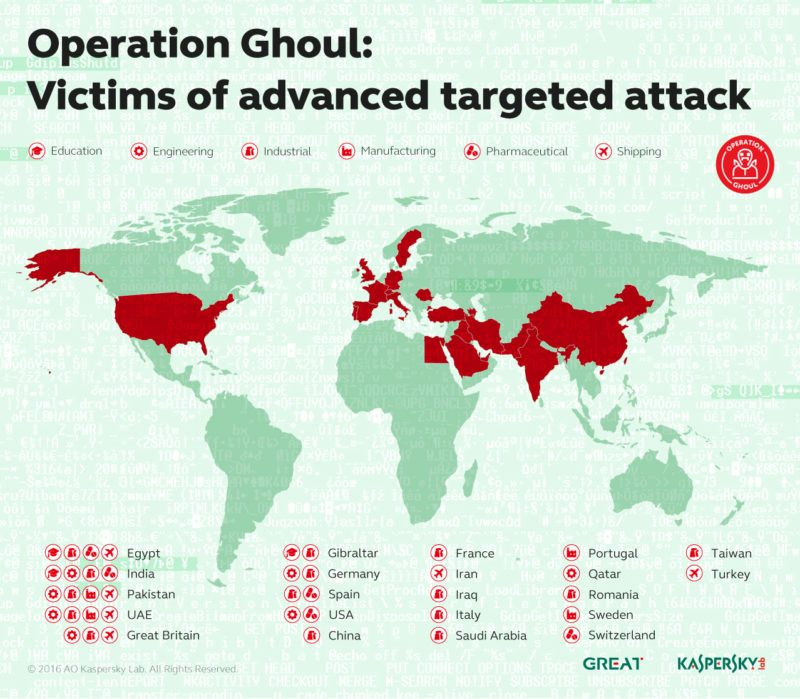
Using spear-phishing emails and malware based on commercial spyware kit, criminals hunt for valuable business related data stored in their victims’ networks. In total, over 130 organisations from 30 countries, including Pakistan, United Arab Emirates, India, Egypt and Saudi Arabia, were successfully attacked by this group.
In June 2016, Kaspersky Lab researchers spotted a wave of spear-phishing emails with malicious attachments. These messages were mostly sent to the top and middle level managers of numerous companies. The emails sent by the attackers appeared to be coming from a bank in the UAE: they looked like payment advice from the bank with an attached SWIFT document, the attached archive contained malware.
Further investigation conducted by Kaspersky Lab researchers showed that the spear-phishing campaign has most likely been organised by a cybercriminal group, which has been tracked by company researchers since March 2015. The June attacks appear to be the most recent operation conducted by this group.
Dubbed Operation Ghoul by researchers, it is only one among several other campaigns that are supposedly controlled by the same group.
“In ancient Folklore, the Ghoul is an evil spirit associated with consuming human flesh and hunting kids, originally a Mesopotamian demon. Today, the term is sometimes used to describe a greedy or materialistic individual. This is quite a precise description of the group behind Operation Ghoul. Their main motivation is financial gain resulting either from sales of stolen intellectual property and business intelligence, or from attacks on their victim’s banking accounts. Unlike state-sponsored actors, which choose targets carefully, this group and similar groups might attack any company. Even though they use rather simple malicious tools, they are very effective in their attacks. Thus companies that are not prepared to spot the attacks, will sadly suffer,” said Mohammad Amin Hasbini, security expert at Kaspersky Lab.
The malware in the attachment is based on the HawkEye commercial spyware that is being sold openly on the Darkweb, and provides a variety of tools for the group – which is still active.





