Every communication service providers (CSPs) surveyed in the Middle East believe robust growth in traffic volumes will continue in the next 2-3 years with 36% expecting traffic to rise by over 50% up to 75%.


Every communication service providers (CSPs) surveyed in the Middle East believe robust growth in traffic volumes will continue in the next 2-3 years with 36% expecting traffic to rise by over 50% up to 75%.

This Russian-speaking actor uses a wide variety of malware implants developed at a rapid pace and in all programming languages imaginable, presumably in order to obstruct attribution.

The results of the M-Trends 2023 report by Mandiant Inc., now a part of Google Cloud, have been announced and …

In the wake of Earth Day 2023, Kaspersky reveals new data on the environmental impact of blocking crypto miners.

The Most Common Root Causes of Attacks Were Unpatched Vulnerabilities and Compromised Credentials, While Ransomware Continues to Be the Most Common “End Game”.

With 60% of organisations taking more than four days to resolve cybersecurity issues, Unit 42’s Global Incident Response Service dramatically reduces time to remediate threats.
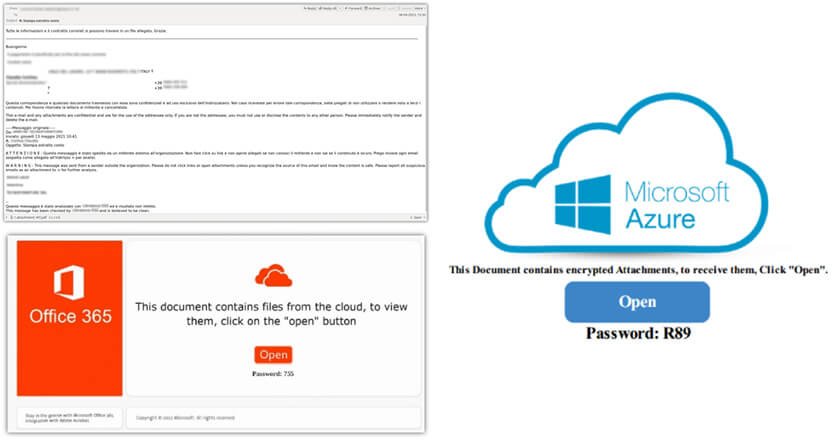
Kaspersky discovered a Qbot malware spike targeting corporate users, spread via a malicious spam-email campaign.

Infoblox rebrand initiatives reflect confidence and business focus, positioning its critical role in securing the networks of some of the world’s largest companies, appealing to both networking and security professionals alike.
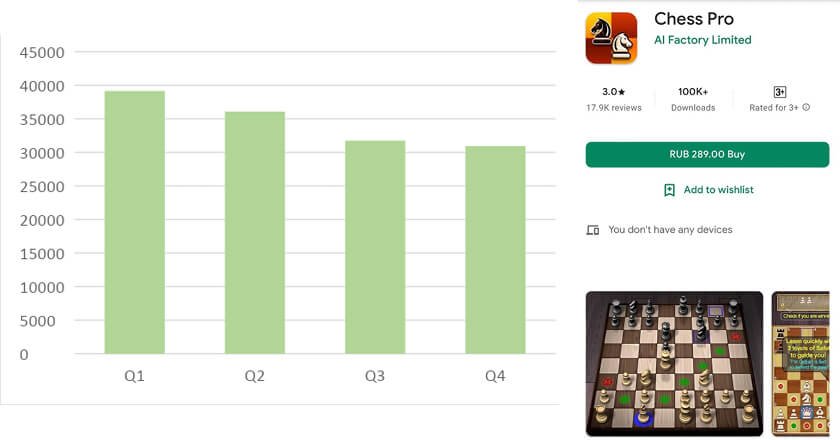
Kaspersky cybersecurity experts have discovered that chess players have been targeted by a range of different attacks from cybercriminals spreading malicious or unwanted mobile programs 一 even on Google Play 一 and Trojans and ransomware disguised as chess applications.
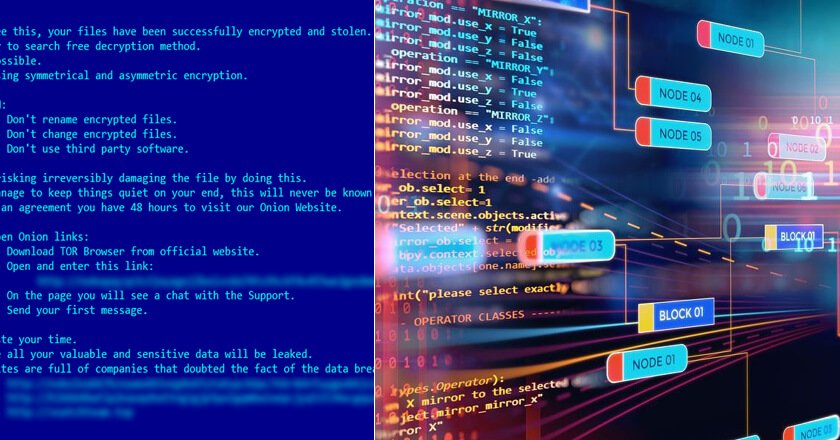
A cybercriminal group used an exploit developed for different versions and builds of Windows OS, including Windows 11, and attempted to deploy the Nokoyawa ransomware.
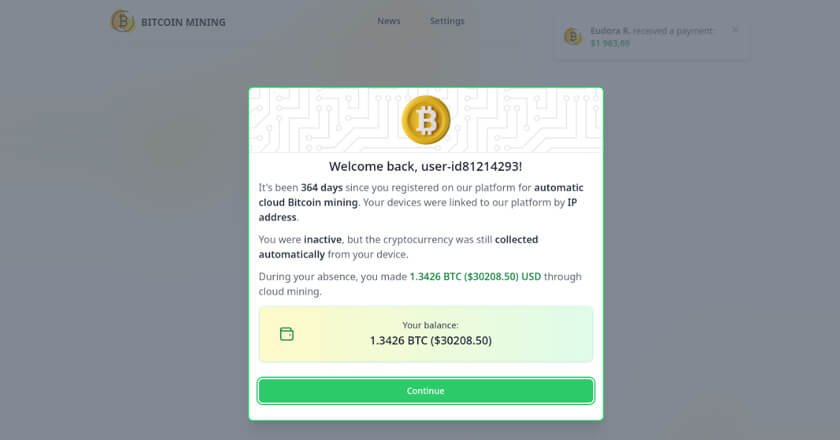
Kaspersky’s anti-phishing systems have prevented 5 million cryptocurrency-related phishing attacks in 2022, increasing by 40% compared to the previous year.

Instead, let us consider technology that does not rely on detection but follows zero-trust principles and assumes all files are malicious. This method works by first verifying a file’s type and identifying any embedded content. It removes any content it considers to be potentially malicious and reconstructs the file using only legitimate components. We call this sanitisation method “content disarm and reconstruction”, or CDR.

NETSCOUT SYSTEMS, INC. (NASDAQ: NTCT), a leading provider of performance management, cybersecurity, and DDoS protection solutions, has released findings from …

A prominent supplier of cloud-based IT, security, and compliance solutions, Qualys Inc. (NASDAQ: QLYS), has issued its 2023 TruRisk Research …

World Backup Day, recognised on 31 March, puts the importance of backing up data in the spotlight for both businesses and individuals, especially as the cyberthreat landscape continues to evolve.

Only 65% of the top 20 Middle East retailers have implemented the minimum level of DMARC protection, meaning 35% are taking no steps to prevent malicious actors spoofing their domain.

Veronica Martin caught up with Raisa Mahomed, AVP Strategic Engagements at Bahwan Cybertek, during GISEC 2023 to discuss the products …

Anita Joseph caught up with Marcus Josefsson, VP EMEA at Nozomi Networks to learn more about cyberthreats that OT & …

Veronica Martin caught up with Ashraf Koheil, with at Group-IB, Regional Director, Middle East, Africa and Turkey during GISEC 2023 …

The average cost of a data breach in the region is $6 million, as per IBM.