A new malicious software programme, advertised for sale on underground forums, claims to mine and steal bitcoins, according to a …


A new malicious software programme, advertised for sale on underground forums, claims to mine and steal bitcoins, according to a …

The U.S. National Security Agency reportedly hacked into over 50,000 computer networks around the world as part of its global intelligence gathering efforts, and also taps into large fiber optic cables that transport Internet traffic between continents at 20 different major points.

Spectrami and Fidelis XPS to reward its channel partners on the sale of Fidelis XPS across the region

Microsoft is opening a landmark 16,800-square foot (1,560m sq) Cybercrime Centre on its Redmond campus to act as an HQ and anchor point for a network of satellite offices that will collect evidence on malware from every continent, the firm has announced.

The creators of a Web-based attack tool called Angler Exploit Kit have added an exploit for a known vulnerability in …
IBM yesterday announced an agreement to acquire Fiberlink Communications, saying the purchase is a key part of a broader mobile-security strategy to provide assurance in transactions conducted via devices such as iPhones and Android smartphones.

The website of a U.S. organization specializing in national and international security policy was compromised with malware that targeted a previously unknown vulnerability in Internet Explorer.

Security researchers have uncovered two unpatched vulnerabilities in Internet Explorer (IE) which have been exploited by attackers in an unusual “watering hole” campaign launched from a U.S.-based website that specialises in domestic and international security policy.

With some commentators labeling the BYOD trend as unstoppable, organisations are now turning to MDM to ensure the security of their networks. But how should MDM be tackled?

CNME is this week set to host its BYOD Summit 2013, the Middle East’s first technology to conference dedicated entirely to the bring-your-own-device trend.

New features include inline sandboxing defenses, malware isolation, phishing education and new platform support

Microsoft might stop updating Microsoft Security Essentials (MSE) antivirus software on systems running Windows XP after next April’s support cut-off, the company has suggested.

Spear phishing is one of the most effective ways to break into a corporate network – and recent studies show that employees can be easily tricked on social media to provide the information needed to launch attacks.
We just found 30 servers that can’t be accounted for. Thirty Internet-facing servers with no malware protection and patchy histories. I need to take a deep breath and figure out just how bad this is and what we can do to stop this sort of thing from happening again.

The new products provide security without compromising system performance.

Windows 8’s user share in October climbed past the 10% milestone for the first time since the launch of the …

A British man has been charged with hacking into US government computers and stealing personal data about thousands of employees, then bragging about it on Twitter.
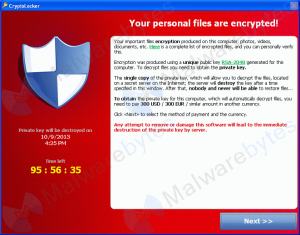
There’s a big threat wiling around on the Internet right now: a particularly nasty piece of ransomware called Cryptolocker.

The biggest cyber-threats facing Middle Eastern businesses today come in the form of targeted attacks, Trend Micro’s Vice President for the Mediterranean, Middle East and Africa regions said today.

Trend Micro will release its findings on the greatest IT security threats to business in the MENA region at GITEX 2013, the company said Sunday.