Iran’s national CERT has warned of a new type of data-wiping malware that bears some of the hallmarks of a cyberattack that severely …


Iran’s national CERT has warned of a new type of data-wiping malware that bears some of the hallmarks of a cyberattack that severely …

In a new twist, spammers have built a botnet that sends SMS spam through infected Android phones, shifting the potentially …

Change in any industry involves conflict. Evolution and revolution in tech this year took place not only in the marketplace …

Security researchers have presented proof-of-concept code capable of accessing the database driving a Microsoft ERP system and then diverting …

Apple has quietly hired Kristin Paget, a former Microsoft security expert who worked as a hacker for the company to …

ESET Middle East has sent out a warning to consumers advising them to be extra cautious and alert when shopping online this …

In 2012 mobility, virtualisation and cloud computing were three big trends that affected change in the way organisations across the …

After gathering analysis of targeted attack data collected between February and September this year, Trend Micro found that 91 percent …

IT managers in corporate and mid-size businesses have to balance both network performance and network security concerns. While security requirements …
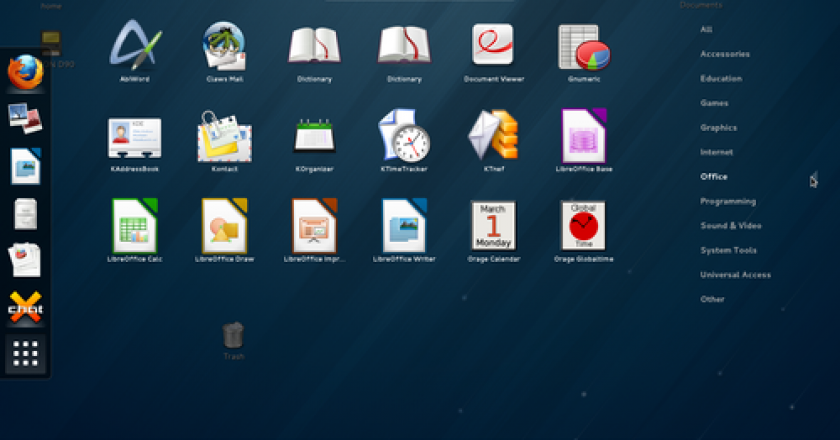
After a number of delays, the beta of the Fedora 18 Linux-based distribution has been released. The beta release date …

Despite vowing that fighting cybercrime is high on its agenda, the European Commission increased its planned cyber security budget by …
Comguard has entered into a distribution agreement with Canada based security vendor, FixMeStick. FixMeStick is a technology innovation that is …

More than half of office workers don’t follow their company’s IT security policies, or aren’t even aware of the policies, …

The advent of mobility and its infiltration on enterprise has birthed a whole new type of security risk, and as …

Cyber criminals are increasingly using .eu domain names in their attack campaigns, according to data from multiple security companies. “Numerous …

In its November 2012 Blue Coat Mobility Study, the company surveyed 350 respondents and found that most organisations allow employees …

Xerox and McAfee revealed new protection against malware and viruses with the first networked multifunction printer to use McAfee Embedded …

Microsoft CEO Steve Ballmer has branded Android ‘wild’ and Apple too ‘controlled’. During a recent conversation with LinkedIn Co-Founder Reid …

With the advent of mobility and the influx of BYOD in enterprise, employers are struggling to keep control of their …

Google’s new app scanner in Android 4.2 Jelly Bean moves the platform closer to Apple’s model of vetting software before …