Stuxnet, the powerful malware that wormed its way in and hobbled Iran’s uranium enrichment efforts, infiltrated the secure networks of the nuclear program via trusted partners, newly public information reveals.
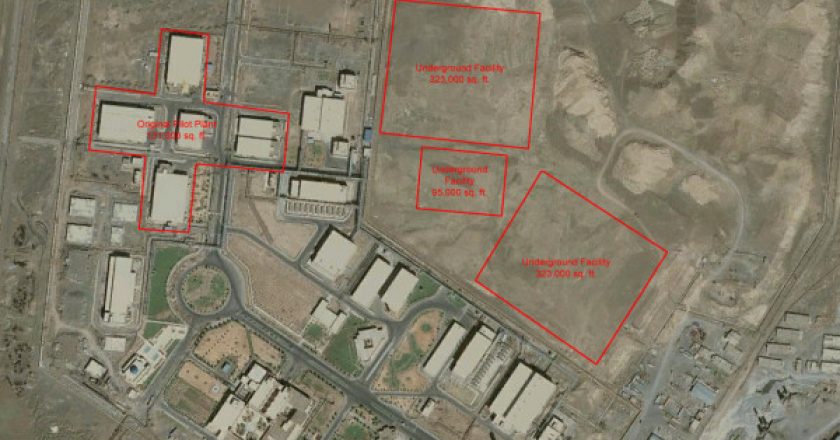

Stuxnet, the powerful malware that wormed its way in and hobbled Iran’s uranium enrichment efforts, infiltrated the secure networks of the nuclear program via trusted partners, newly public information reveals.

Researchers from Symantec have found and analysed a version of the Stuxnet cyber sabotage malware that predates previously discovered versions …

The company’s groundbreaking platform provides passive, real-time monitoring for industrial control systems, addressing deep-rooted cybersecurity blind spots in critical infrastructure. …

Arun George, International SecOps Sales Leader, CyberRes, a Micro Focus Line of Business on the company’s participation at GITEX and how it is helping customers address the expanding cyber-attack surface.

Cyberattacks Become Part of the Military Arsenal.

New Approaches for ‘Air Gapped’ IT and OT Environments for Critical Infrastructure.

Abhijit Mahadik, Director, Cybersecurity & Infrastructure, UAE & KSA, Raqmiyat, speaks to Anita Joseph, Editor, SAME about the evolving cybersecurity landscape, the threats organisations need to watch out for and how the security priorities of organisations have shifted since the pandemic last year.

Group-IB launches regional HQ in Dubai. City becomes home to its MEA Threat Intelligence & Research Centre.

Cybersecurity solutions provider Bitdefender protecting has announced its participation in the 39th edition of GITEX Technology Week, to be held in Dubai, UAE, from 6th to 10th October.

Tenable has discovered a critical vulnerability in Siemens STEP 7 TIA Portal, design and automation software for industrial control systems.

Removable USB media devices such as flash drives pose a significant – and intentional – cybersecurity threat to a wide array of industrial process control networks, according to a recent study.

Vinod Vasudevan, Co-founder and CTO, Paladion. discusses the rise of a new era where organisations and individuals alike are exposed to security risks and vulnerabilities brought by connected technologies.

According to recent reports, hackers likely gave away hundreds of thousands of dollars in potential sales in the black market when they leaked valuable cyberweapons that were allegedly stolen from the US National Security Agency.

Patching, backups, firewall configuration… when it comes to security, make sure you take care of your infrastructure before you invest in next-level tools.

As a first-time participant at GISEC, AccessData aims to use the event as a platform to showcase its key capabilities in the security space and connect with potential customers.

A cyber-espionage group with a toolset similar to ones used by U.S. intelligence agencies has infiltrated key institutions in countries including Iran and Russia.

For the past two years, a team of Iranian hackers has compromised computers and networks belonging to over 50 organisations from 16 countries, according to research from IT security firm Cylance.
After a long summer break, CNME kicked off its long-anticipated event season with the return of the fifth annual Enterprise Security 360 Roadshow. Reaching Riyadh, Dubai and Doha, the show covered a range of issues that are never far from the thoughts of Middle Eastern CIOs. CNME reports from the UAE leg of the show.

In addition to dealing with cybercriminals and hacktivists, enterprise security managers must pay increasing attention to avoid becoming collateral to nation-state cyber-warfare. Do recent high profile attacks on the region indicate that Middle Eastern businesses are at greater risk of attack, and what damage can cyber warfare inflict?