With the right approach organisations can keep data and infrastructure safe under a completely different office dynamic, says Hadi Jaafarawi, managing director – Middle East, Qualys.
Prior to the emergence of COVID-19, technical teams across the region would have likely been planning for a year in which they addressed the finer points of cloud computing — what it meant for their organisation and how to leverage it to facilitate cost management and business agility.
Cybersecurity professionals would have been occupied with how they adjusted their threat postures to accommodate new architectures. Curiously, now that the pandemic has forced governments to keep us safe by imposing lockdowns, CISOs and their teams have more or less the same challenge in front of them: keep data and infrastructure safe under a completely different office dynamic. With remote working becoming increasingly widespread, team members need to find new ways of collaborating, to defend against a threat landscape that shows no compassion for our shared challenge.

Adapt to survive
Crises always demand shifts in priorities. We must now protect ourselves and others from harm by working in new ways. These necessities are likely to persist, and we must adapt to ensure that our isolation does not yield secondary crises, such as the many economic ones that I am sure occupy your mind as you read this.
From a cybersecurity perspective, we can be certain bad actors will look to exploit the fact that new, unprotected endpoints have now suddenly been thrust upon many corporate domains. An important element of control has been obliterated by necessity, even as it has given rise to new efficiencies. After all, many have argued for some time that working from home has the potential to increase productivity and talent retention.
But we need to beware. Employees’ private devices must be recognised for what they are: weak links in the security chain. Every time someone initiates a session with a remote applications host, they are fodder for attackers. Any time data is in transit, it is vulnerable to hijackers.
The first thing security teams need to do is to take control of the new devices. Whether by bulletin, or by one-to-one communication, they must instruct employees how to patch and update operating systems and install security tools that meet with corporate standards. Such work needs to be monitored and verified to ensure that the weak links have been sufficiently shored up.
Do you feel vulnerable?
Many of the challenges presented by such approaches will centre on getting to grips with large numbers of new devices, understanding their vulnerabilities and clearly communicating the necessary steps to fix such issues to non-technical employees.
Bandwidth may also be a challenge, as will verification and enforcement. And consider that such patching must occur periodically, which means that verification and enforcement are also ongoing. Every day, the cybercriminal discovers more software vulnerabilities to exploit, and security teams — and under the new work paradigm, those teams extend to every remote worker — need to be equal to their cunning.
Normally, IT teams curate patches from the larger vendors to deploy in a single dose. While this simplifies the task, it works better when technical teams have tight control over devices, to allow compatibility testing, and rollbacks if necessary. Under remote-working conditions, IT has the challenge of first establishing what other software is installed and vetting configurations to ensure a smooth patching process. These are not simple tasks when being performed over the wire.
These challenges still exist for those enterprises that had the foresight to bring employee devices up to code before lockdowns were enforced. Because of ever-emerging vulnerabilities and the volatile nature of today’s regional threat landscape, up-to-code devices are unlikely to remain so for long.
Look to the cloud
So, is there a simpler way to manage all of this? Under the new remote-working model, can teams get single, unified views of device ecosystems in a way that allows them to take action in an informed and targeted manner on a device-by-device basis? Is there a way to automate updates?
Yes, yes and yes. Cloud services provide a useful platform for an IT team to get a bird’s-eye view of all devices on their network. Dashboards allow at-a-glance assessment of the level of preparedness of each machine, and other cloud services deliver the means to automate patching with adherence to a regular schedule. Tools also allow for granular control over prioritisation that matches any mechanism previously used in the on-premises environment.
Through platforms such as this, we start to address many of our remote-working challenges as they relate to security: complex monitoring is taken care of; verification is delivered through automation; and enforcement is a given. And so, we return to the controlled ecosystem we enjoyed previously, courtesy of the cloud.
And because we can guarantee the same measure of protections as previously, businesses that rise or fall on their ability to remain compliant with a range of national, regional and international regulations, can continue to operate unabated. Unified insights into every corner of the corporate network are key to business continuity, as is the ability to replicate previous environments where practical and necessary.
Through the cloud, isolation need not mean the same as it used to. Control endures, along with the means to support employees and allow them to remain productive as we work through the challenges ahead. With such capabilities in place, businesses keep thriving and growing as before. Economies survive. And all of us can take some little comfort that when we emerge from the crisis, a return to normal will follow swiftly.
This week
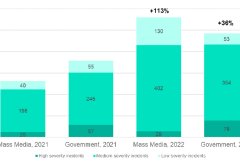
Security Operations Centres to face greater challenges in the coming year
0 23888SOCs to face greater challenges from cybercriminals targeting governments and media.
The new normal: Navigating cybersecurity and remote working amid COVID-19
0 5056The coronavirus (COVID-19) pandemic has forced businesses to undergo seismic changes in the way they operate. As flexible policies become standard and remote work becomes a norm, another important challenge is taking the spotlight – cybersecurity.
How Lenovo DCG is transforming productivity in times of remote working
0 6097Dr. Chris Cooper, Director, Data Center Group (DCG), Lenovo META, shares insights into the IT-giant’s business continuity strategy in times …





