 Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.
Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.
RLO is used in bi-directional text encoding systems as a way to mark the start of text that should be displayed from right to left. This is commonly seen in applications and software that are able to correctly display Arabic, Hebrew, Persian, and Yiddish – among other languages.
RLO as a means of attack has been around since late 2009, but gained wider attention in 2011 when the technique was used to spread the Bredolab family of malware. While previous attacks using RLO have been grand schemes, F-Secure’s discovery shows the process being used simply to hide the actual file extension.
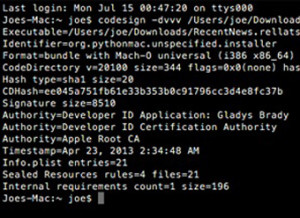
Examination of the malware itself shows code that enables an attacker to take continuous screenshots and record audio, while waiting for additional commands. It’s written in Python and uses py2app for distribution. The code is signed by a legitimate Apple Developer ID, which may help it bypass some of the controls on a Mac depending on how the user configured their security settings. At the same time, due to the way the malware is encoded, the RLO will also impact the quarantine notification, forcing it to display the warning with all of the text reversed.
Once executed, assuming the attack makes it that far, the malware displays a PDF file (such is the case for the variant discovered by F-Secure) that acts as a decoy while a CRON job and hidden folder in the user’s home directory is created in the background. The malware will then connect to various sites to receive the address of the command and control (C&C) server. F-Secure observed two videos on YouTube that contained the C&C address within the description field.
According to the stats from YouTube before the videos were removed, the malware had infected more than 1,000 systems.
As a measure of protection, it’s been advised that the Security and Privacy preferences be configured to only allow apps from the App Store to run without explicit authorisation. Once the Apple Developer ID is revoked, Gatekeeper will also flag this malware (and other variants signed with the same ID) as a problem.





