This spike reflects a similar trend in the Middle East region, which projected a two-fold hike (103%) in Rootkit detections, as compared to the first five months of last year.


This spike reflects a similar trend in the Middle East region, which projected a two-fold hike (103%) in Rootkit detections, as compared to the first five months of last year.

Attacks on Middle Eastern government agencies are mainly carried out by APT groups (56%), covertly establishing themselves in the victim’s infrastructure for the purpose of cyberespionage.

Behavioural correlation of events from multiple sources helps to act faster, get more attack context and start looking for previously unseen activities.

On Artificial Intelligence Appreciation Day, Anita Joseph, Editor, Tahawultech.com, spoke to technology industry visionaries to find out what they think …

As the automotive industry moves towards a future of connected and autonomous vehicles, ensuring robust cybersecurity is of paramount importance. …

With Finesse and JetPatch working together, businesses can confidently navigate their digital journeys while safeguarding their digital infrastructure.

Kaspersky unveils a comprehensive report highlighting the increasing peril faced by small and medium-sized businesses (SMBs) in the current cyberthreat landscape.

Unified view of identity and entitlement risks across Active Directory and Azure AD helps reduce the risk of identities being used in cyber attacks.

As an executive level member, Tenable will champion preventive security approaches, helping organisations understand and reduce cybersecurity risk across their entire attack surface—from the cloud, IT, OT, identity systems and beyond.

Adrian Taylor, VP EMEA at A10 Networks, has penned an exclusive op-ed that highlights the issues facing commercial data centre …
Proper configurations of a security solution are crucial to prevent it from disabling or even abusing it – a tactic often seen to be employed by APT groups/actors.

Gaurav Mohan, VP, SAARC & Middle East, NETSCOUT explains how depending solely on endpoint detection is not enough to protect …

Cybersecurity specialists are invited to join the global event to discuss the evolving landscape of IT security and share their expertise on the latest and most sophisticated cyber threats.

Anita Joseph caught up with Aloysius Cheang, Chief Security Officer at Huawei Middle East and Central Asia, to find out …

OPINION: Tarek Naja, Solutions Architect, at Qualys, believes that in order to overcome the complexities that come with moving workloads …

Cisco has announced the launch of a new Full-Stack Observability platform—a vendor-agnostic solution that harnesses the power of the company’s …

Following the report on the Operation Triangulation campaign targeting iOS devices, Kaspersky researchers have released a special ‘trianglecheck’ utility that …

Cisco Talos has released its cybersecurity report for the first quarter of 2023, highlighting the most common attacks, targets and …
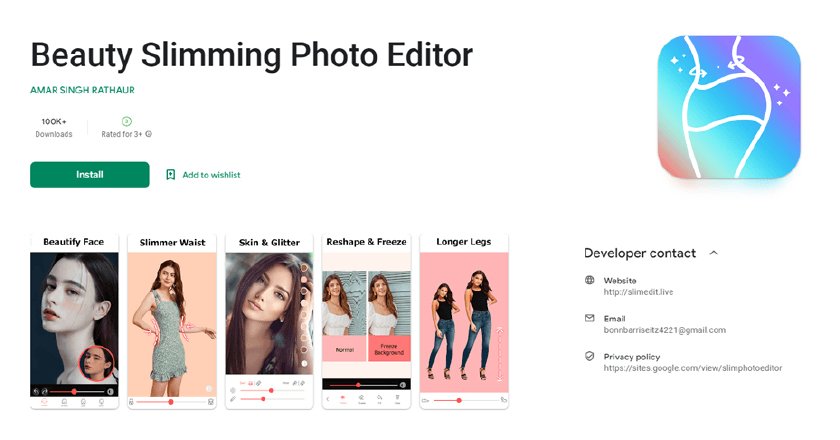
The new Trojan family, Fleckpe, is Kaspersky’s latest discovery that spreads via Google Play under the guise of photo editors, wallpaper packs and other apps. In fact, it subscribes the unwitting user to paid services.
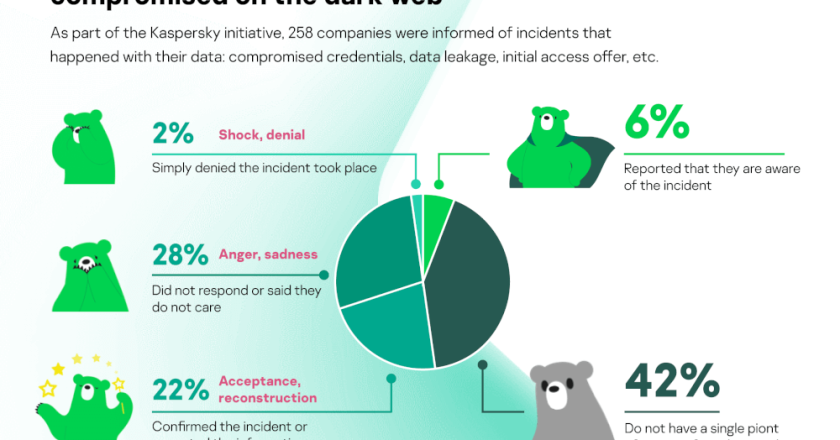
At the beginning of 2023 the share of users attacked with spyware in the Middle East increased by 11.8% from …