A newly discovered flaw in widely used networking software leaves tens of thousands of computers potentially vulnerable to an attack …


A newly discovered flaw in widely used networking software leaves tens of thousands of computers potentially vulnerable to an attack …
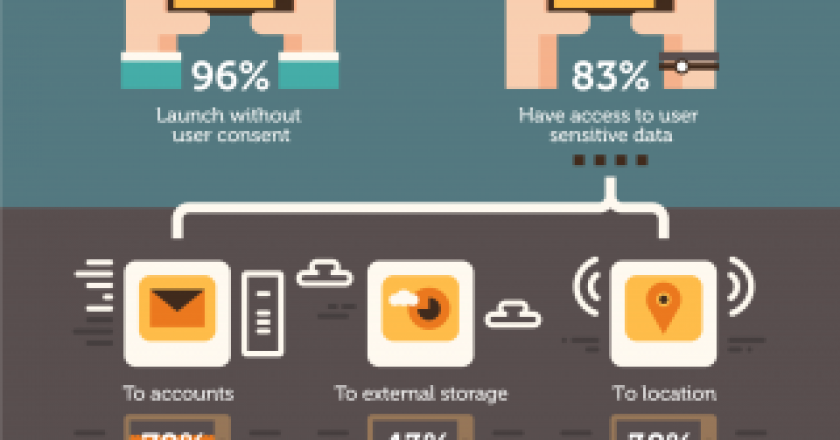
Digital clutter is growing due to an explosion in application usage and advances in the storage capacity of devices. But …

Mimecast has announced its participation at the 4th Gulf Information Security and Conference (GISEC), which is being held from May 21st to May 23rd, 2017 at the Dubai World Trade Centre.

The ‘Wannacry’ ransomware attack will be a hot topic on the main conference floor and in the corridors of the Dubai World Trade Centre (DWTC) when the 4th Gulf Information Security Exhibition and Conference (GISEC) opens its doors today.

Recent research by Symantec found that an unsecured Internet of Things (IoT) device is attacked within two minutes once connected to the Internet

A group of hackers that previously leaked alleged U.S. National Security Agency exploits claims to have even more attack tools …
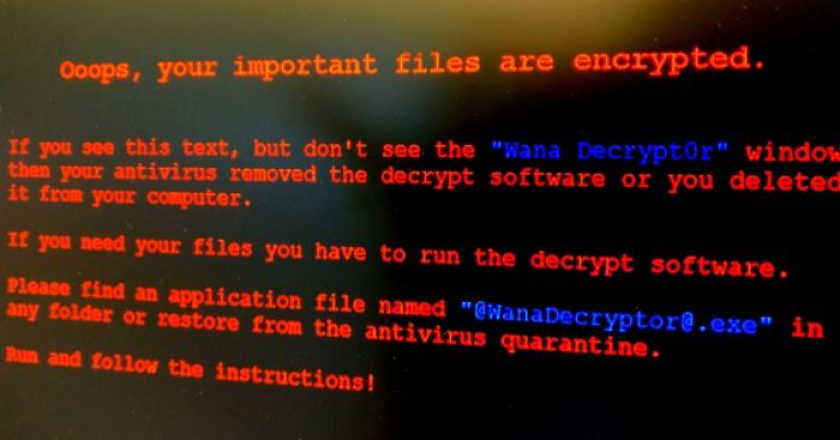
As security researchers investigate last Friday’s massive attack from the WannaCry ransomware, they’ve noticed clues that may link it with a North …

Carbon Black has announced its participation in the Gulf Information Security Expo & Conference (GISEC 2017) for the third consecutive year, which will be held at the Dubai World Trade Centre from 21st to 23rd May 2017.

The ransomware, christened WannaCry, has struck systems around the world on Friday. Tahawaul Tech spoke to some of the users and security pros to find out what local companies can do to combat this new threat.

Microsoft on Sunday said a software vulnerability stolen from the U.S. National Security Agency has affected customers around the world, …

The UAE’s Telecommunications Regulatory Authority (TRA) has urged users to be vigilant after a fast-moving wave of ransomware swept the …

This week’s attacks leveraging the WannaCry ransomware were the first time we’ve seen an attack combine worm tactics along with …
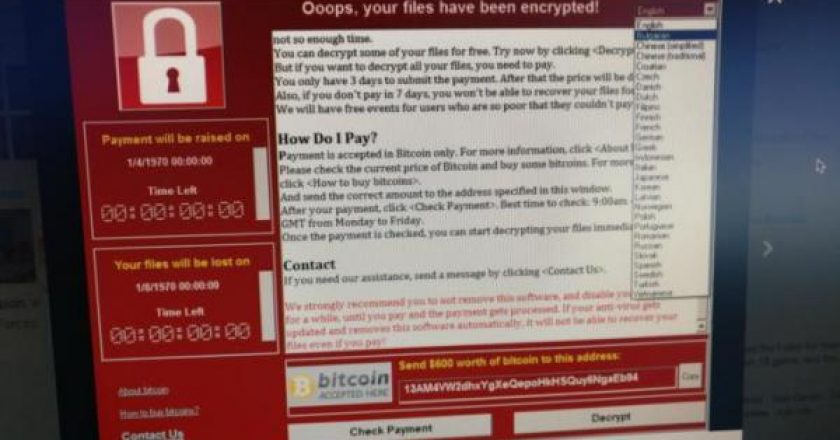
Users of old Windows systems can now download a patch to protect them from this week’s massive ransomware attack. In …
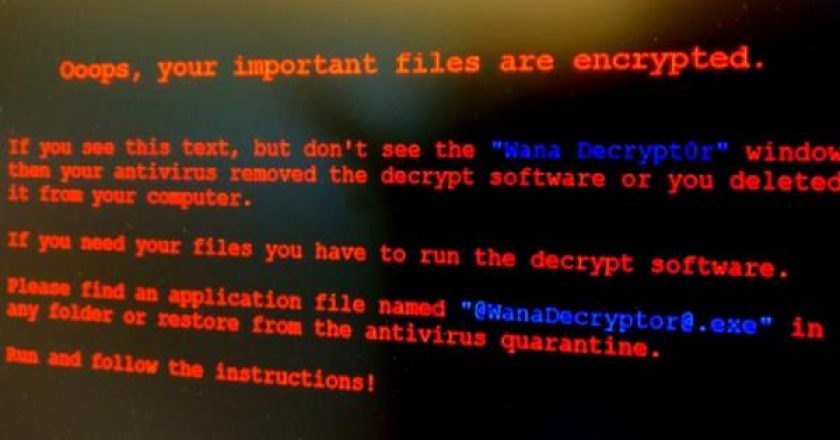
Friday’s unprecedented ransomware attack may have stopped spreading to new machines — at least briefly — thanks to a “kill …

Microsoft released security patches on Tuesday for 55 vulnerabilities across the company’s products, including for three flaws that are already …

According to Kaspersky Lab’s “Spam and phishing in Q1 2017” report, the world’s largest spam botnet, Necurs, demonstrated a relative …

With an intense focus on boosting the IT security, communications and technology industries in the Middle East region, UAE-based Bulwark …

Help AG has extended its long-standing partnership with Palo Alto Networks by joining the vendor’s Traps Managed Security Service Provider …

Eddie Schwartz, Executive VP of Cyber Services, DarkMatter, outlines why we need to turn the tables on cyber thieves. The …

A recent report has revealed that despite seeing an improvement in the UAE’s internet security threat profile in 2016, the country is still a key target for hackers.