Network Solutions is investigating an attack by a pro-Palestinian hacking group that redirected websites belonging to several companies.
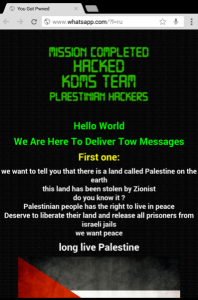

Network Solutions is investigating an attack by a pro-Palestinian hacking group that redirected websites belonging to several companies.

Alex Holden, founder of security company Hold Security, is in the business of bringing companies bad news.

Google has removed an application from its Play store that purported to be AdBlock Plus, a well-known application that blocks online ads.
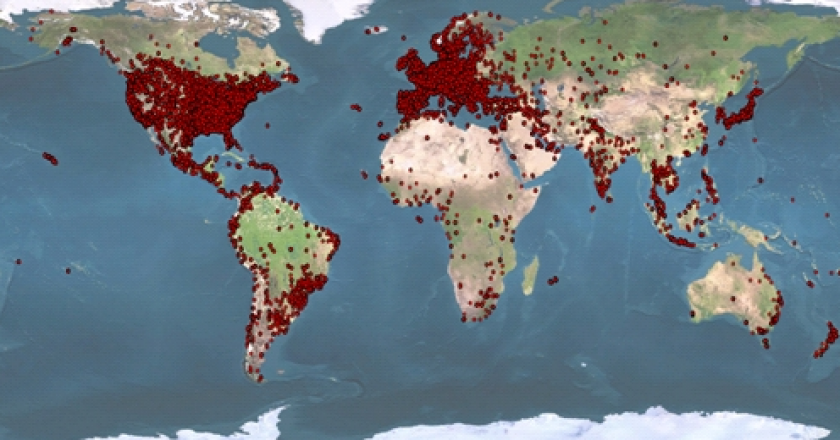
The cyber-criminals behind ZeroAccess, one of the largest botnets in existence, have lost access to more than a quarter of the infected machines they controlled.

The Federal Circuit Court of Australia has awarded Microsoft $304,994.95 in damages after Paul McLane, trading as Software Paul, was …
According to new poll conducted on MacWorld, 64% of readers think that iOS 7 is great. However, there are some people who are not so keen.

A group of between 50 and 100 professional hackers operating out of China has been systematically targeting businesses, military and government agencies around the world since at least 2009, security vendor Symantec said in a report released on Tuesday.

One of the world’s leading online security and privacy experts has warned that unprotected remote working and social media use can pose significant risks to both individuals and businesses across the Middle East.

Much of what Apple offers enterprise workers and their IT departments in the new iPhone 5S and 5C comes by virtue of its new iOS 7, first announced in June.

The US is engaged in a wide-ranging campaign of cyber-operations against foreign targets, launching over 200 in 2011 alone, budget …
Mobile and tablet devices have become real hubs for all sorts of personal information, photos, work files, music, videos and …

In a much-publicized recent case, scientists at Georgia Tech managed to get a specially crafted app that could perform all sorts of malicious activities app-aptly named Jekyll-onto the App Store

Smartphones are a treasure trove of personal information and it doesn’t take much for people who would mean you harm to get at all that sensitive data.

VMware’s NSX network virtualization platform, expected out by year end, will have a key security tool for deploying security software and services to VMware-based virtual machines.

About half of global organizations have suffered a cyberattack in the last year, said a report released on Tuesday by the Information Security Media Group and Bit9.

Twitter, The New York Times and other prominent websites were struck by a powerful cyberattack that continued affecting other websites into Tuesday evening, directing visitors to a site purportedly controlled by the Syrian Electronic Army (SEA).

AccessData this week announced that it has signed a distribution agreement with ARM, which specialises in cyber-security and other consumer-related IT software products in region.

In the never-ending battle of iOS versus Android, one of the biggest marks against Google is that its Play store isn’t regulated enough for the novice smartphone user.

As Windows 8 struggles to take off, Microsoft has decided to hire a new ad agency to handle the digital promotion of both the operating system and Microsoft Surface tablets.

Rapid 7 this week unveiled a new set of tools designed to help businesses better judge the overall effectiveness of existing security controls and the risk associated with users across the organization.