A second vulnerability that can be exploited to modify legitimate Android apps without breaking their digital signatures has been identified and publicly documented.


A second vulnerability that can be exploited to modify legitimate Android apps without breaking their digital signatures has been identified and publicly documented.

A noisy malware campaign against South Korea is revealing deeper secrets.

If 3,370,780 UAE residents use Facebook, and 80 percent of those replicate their passwords for other accounts, then the opportunity for cyber theft and hackers to infiltrate personal accounts is extremely high.

As more employees demand to use their personal devices for work, IT managers are struggling to both accommodate them and safeguard confidential company data.
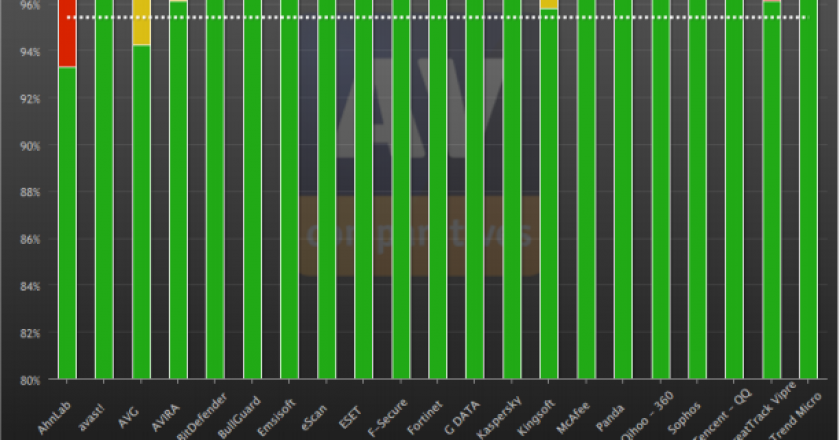
Kaspersky Internet Security 2013 and Trend Micro Internet Security 2013 reportedly blocked 100 percent of malicious online attacks in a recent real-world protection test.

South Korea has come under attack from a vicious new disk-wiping Trojan that is almost certainly part of a long-term campaign against organisations in the country, Symantec has said.

With the previously $40,000 Carberp Trojan’s source code now freely available, experts expect exceptionally destructive variants of the malware to flow onto the Internet.

It was only a matter of time before it happened and now it has – ransom malware has successfully made the jump from the PC world, where it torments millions of Windows users, to the mobile world, where it has similar designs on Android.

By Tom Kaneshige CIO (US) Are you blacklisting rogue or time-wasting apps? Are you tracking voice, data and roaming usage? …
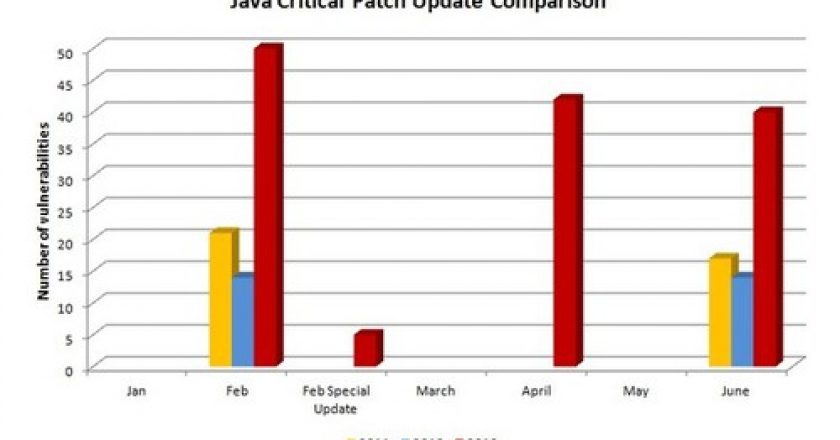
Oracle released a huge update for the virtually ubiquitous software, but attackers aren’t done exploiting Java as the weakest link in the security chain, and Oracle isn’t securing it fast enough.

The things that cyber-criminals are able to do with your phone are terrifying.

The average organisation believes it would spot a data breach in 10 hours, a McAfee global survey of IT professionals has found. But is that result good, indifferent or an indication of the downright complacent?

Last week’s attack on the Virgin Radio Dubai website could have provided cyber-criminals with a springboard from which to launch …

Thursday afternoon, a bombshell dropped: Two leading reports claimed that the U.S. government has been spying on emails, searches, Skype calls, and …

Law enforcement authorities recently seized over 1,000 pirated Xbox 360 games from local retailers, following three raids in Abu Dhabi, …

Microsoft and the U.S. Federal Bureau of Investigation have taken aim at a botnet network based on malware called Citadel …

Android smartphones and tablets are under attack, and the most popular tools developed to protect them are easily circumvented, according …

The first three months of 2013 have seen a surge in spam volume, as well as large numbers of samples …

Oracle plans to make changes to strengthen the security of Java, including fixing its certificate revocation checking feature, preventing unsigned …