Apple on Friday released its own update for Java 6 for Mac users running OS X Snow Leopard, matching Oracle’s …


Apple on Friday released its own update for Java 6 for Mac users running OS X Snow Leopard, matching Oracle’s …

HP announced last week that it plans to use its recently unveiled SDN controller to distribute its TippingPoint intrusion prevention …

Kaspersky Lab on Wednesday made its bid to reduce the complexity associated with managing IT security processes in corporate environments, …

Cyber criminals have moved beyond the traditional PC, targeting Android, social media and even the Mac OS X with new …
In February 2012 the Anti-Economic Crimes Department of the Dubai Police carried out an enforcement action against a computer and …

Security shot up the priority list of not just CIOs but also higher management in 2012 as the world witnessed …

Following on from last year’s Flashback Trojan incident, which saw 600,000 Mac users infected with malware through a Java loophole, …

The Virut botnet suffered a major setback last week, after it was announced that many of the domain names used …

Researchers from a Poland-based vulnerability research firm on Friday announced that they had found vulnerabilities in Java 7 Update 11 …

Following a failed evaluation by a German software security testing firm, Microsoft vowed on Wednesday to improve two of its …

Oracle’s bad Java week got worse on Wednesday, after it was announced that a previously unknown flaw in the programming …
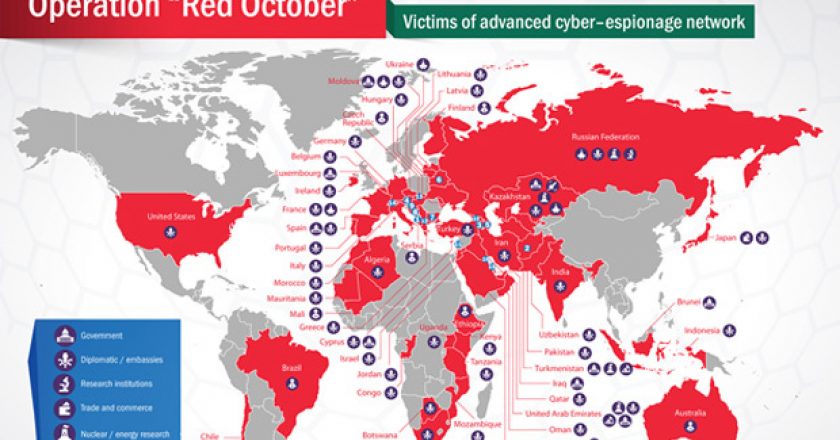
A cyber espionage network has been allowed to flourish in Eastern Europe, former Soviet republics and Central Asian countries since …

Microsoft will deviate from its regular Internet Explorer repair schedule today by releasing a patch for older versions of its …
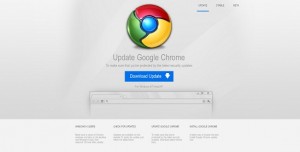
Following Google’s recent upgrade of Chrome, a new wave of bogus updates has been set upon the Internet by cyber …

Though U.S. officials have consistently blamed Iran for the ongoing stream of distributed denial of service attacks (DDoS) against major …

Among your typical New Year’s resolutions–lose weight, stop smoking, be happier–you should consider making some pledges to better secure your …

Java 6 will be retired from security support in less than two months, and users and businesses should prepare now …

Adobe plans in February to close a dangerous hole in its Shockwave application that causes the application to be downgraded …

Europe’s top data privacy agency has launched a formal investigation into Microsoft’s privacy policy. Microsoft confirmed on Tuesday that it …

Cyber espionage is nothing new. So a report from the Defense Security Service (DSS) about efforts in foreign countries to …