By Andrew Rose, Resident CISO, EMEA at Proofpoint

Why do people click on malicious links?
It’s a question that’s been around for as long as links have existed.
We think of cyber criminals as sitting in basements, plotting to subvert technology by breaking through the firewall, but the reality is that the problem is a human one. Technology is actually quite effective at withstanding attacks, so the attackers target the most vulnerable spot – the user. In fact, at Proofpoint we see 94% of cyberattacks starting via email, and more than 99% of those requiring human interaction to activate and enable the attack. In addition, Proofpoint’s recent regional research found that 55% of CISOs/CSOs in the UAE believe that human error was one of the risk factors for their organisation.
Hence, it is crucial to look at the science and psychology of these attacks to see why, despite all of the investment in education and awareness, these cliché’d attacks are still effective.
The Attackers Intention

There are three main ways attackers are trying to gain advantage: by getting the user to run their code, by encouraging the user to hand over credentials, or simply instigating the direct transfer of money or data to the attacker.
There’s been a recent trend to make attacks more complex, in an attempt to place distance between the initial email and the malware to try to bypass malware detection, but these attacks still need human interaction.
How Attackers Make People Click
Attackers want employees to forget the security awareness training they’ve had, and make a poor decision which will enable them to progress their attack. There are three aspects that they leverage to create this failure scenario – Emotion, Trust & Fatigue.
Let’s tackle these in reverse order:
1 – Fatigue
Ask any Chief Information Security Officer (CISO): it’s an anecdotal truth that a high proportion of cyberattacks occur in the last day of the week. This is because any successful breach will give the attackers the whole weekend to exploit their access while the victim firm is likely running at a lower level of vigilance. In addition, by the end of the working week users are more likely to make a poor choice as there’s a higher chance they are fatigued.
Another aspect of fatigue is the ‘overwhelm’ effect. If the attacker knows their action will set off an alarm – why not trigger ten thousand false alarms first, until the target becomes overwhelmed and desensitised, and then conduct the real attack.
2 – Trust
The second lever that attackers utilise is trust. When faced with an array of choices, trust is another shortcut that our brains use to make rapid decisions. If we see an association with a brand or person we trust, then the communication gathers more credibility and the threshold required to make us click or interact is lowered.
Examples of this are widespread, and it’s why fake emails show up claiming to be from ‘DHL’ and ‘Amazon’ much more frequently than other delivery or online stores. The same trust is leveraged even in the location of the malware, and Proofpoint’s research shows users are four times more likely to click on malicious links if they point to Microsoft SharePoint, and ten times more likely to click if it points to Microsoft OneDrive.
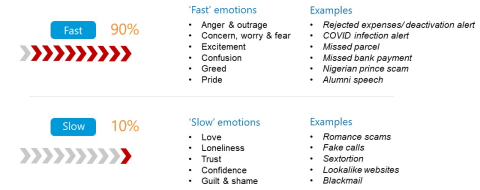
3 – Emotion
Attackers can actively set out to trigger emotional responses so that the target will make rapid decisions, bypassing people’s rational thoughts, and increasing their likelihood of clicking on a link when they really know better.
The vast majority of these emotional responses are intended to be ‘fast’ in order to trigger that rapid emotional response, where the rational brain is not invited to contribute. This is why people click, despite knowing better. Subjects such as ‘your package is about to be returned to depot’, ‘your Netflix account is about to be suspended’, or ‘your expenses have been rejected’ are some examples of how these lures capitalise on urgency.
How To Prepare Employees To Deal With Attacks
Like we’ve seen, attackers are specifically targeting people’s emotions to bypass their higher reasoning as Organisations must ensure their employees recognise that if they are reading an email that elicits an emotional response, they should immediately be wary and the stronger the push, the more careful and thoughtful they should be.
Also push for a ‘trust, but verify via a different channel’ model whenever a staff member detects any hint of suspicion around a communication.
If organisations focus on people as a primary line of defense and remember that the attackers are ultimately focusing on the human and not the technology, they can better protect the enterprise.
Each user has the power, they can choose to not let the attacker manipulate their emotions and abuse their trust – but only if they know what to look for. Being wary, aware and thoughtful as they read email, looking for emotional triggers, and having a ‘trust but verify’ mindset, can go a long way in helping prevent those unwanted clicks.





