Kaspersky Lab experts are registering important changes in the operations of the infamous Gaza Cybergang, which is actively targeting multiple …


Kaspersky Lab experts are registering important changes in the operations of the infamous Gaza Cybergang, which is actively targeting multiple …

About one year ago the No More Ransom initiative was launched by the Dutch National Police, Europol, McAfee and Kaspersky …

The study found that staff would rather put organisations at risk than report a problem because they fear punishment.

A wave of ransomware swept across Europe at an incredibly rapid pace, grinding business to a halt at banks, airports, pharmaceutical companies, government offices, service providers, utilities and more, security researchers said.

Late on 27 June, the New York Times reported that a number of Ukrainian banks and Ukrenergo, the Ukrainian state …

The NotPetya ransomware that encrypted and locked thousands of computers across the globe yesterday and today is, in reality, a …

Tuesday’s massive ransomware outbreak was caused by a malicious software update for M.E.Doc, a popular accounting software used by Ukrainian …

The Internet of Things (IoT) continues to gain a strong footing in the GCC across different sectors ranging from manufacturing and transportation to energy, according to a recent report by Booz Allen Hamilton.

People are exposing themselves to identity theft or financial attacks by sharing financial and payment details (53%), scans of their passports, driving licenses and other personal documents (71%) or passwords (44%).

Cyber-attacks are inevitable and companies have no option but to prepare themselves to respond to the attacks appropriately, an international cybersecurity expert has said.
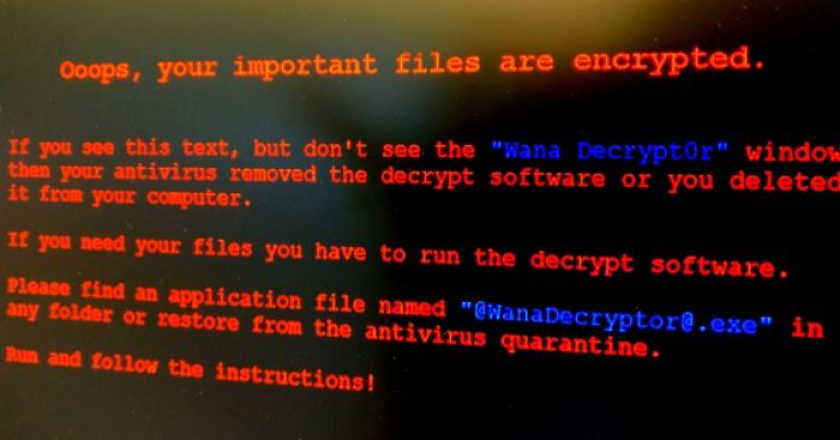
As security researchers investigate last Friday’s massive attack from the WannaCry ransomware, they’ve noticed clues that may link it with a North …
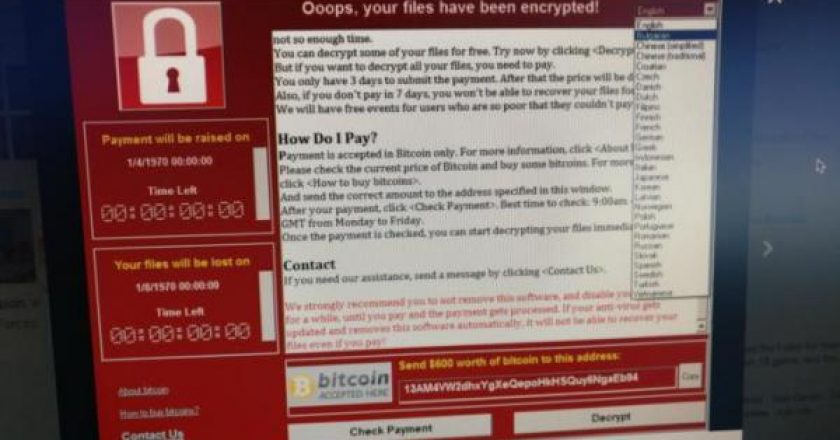
Users of old Windows systems can now download a patch to protect them from this week’s massive ransomware attack. In …

According to Kaspersky Lab’s “Spam and phishing in Q1 2017” report, the world’s largest spam botnet, Necurs, demonstrated a relative …

As companies and individuals across the globe increasingly feel the pressure to protect crucial information online, cybersecurity firms at the …

Aptec, an Ingram Micro company, has announced its inaugural participation at the upcoming 2017 Gulf Information Security Expo and Conference …

The Index for the second half of 2016 demonstrated a positive trend: the number of people who are concerned about their security, and are ready to protect themselves against cyber threats, is constantly growing.

The costs associated with cyberattacks on the financial sector are rising as organizations face increasingly sophisticated threats. New research by Kaspersky …

How to survive a ransomware attack unscathed

SCOPE Middle East has announced that it is now a member of the HID Advantage Partner Program, a loyalty-based programme which advances a partner’s relationship with HID Global.

DDoS attacks are vastly bigger now. Here is what you need to do to protect yourself and your network.