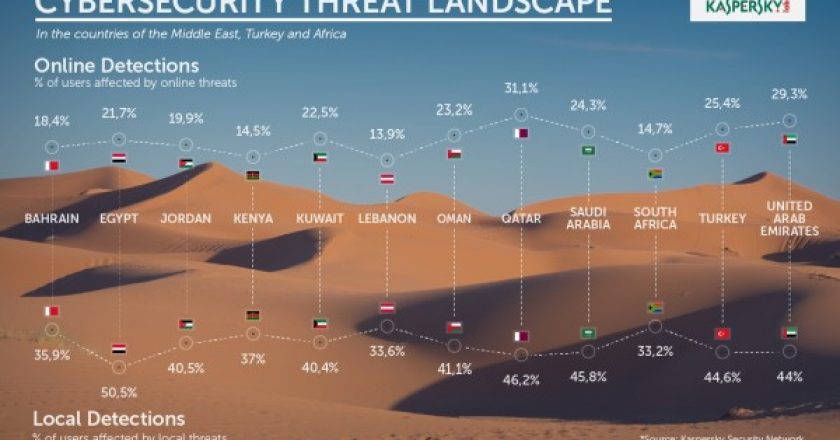
Cyber criminials are becoming more organised and taking higher bounties. Kaspersky Lab’s Cyber Security Weekend for the Middle East, Turkey and Africa kept CNME abreast of changes in the security landscape and predicted what we can expect in the coming year.