Cybercriminals have developed a Web-based attack tool to hijack routers on a large scale when users visit compromised websites or …


Cybercriminals have developed a Web-based attack tool to hijack routers on a large scale when users visit compromised websites or …

According to a new survey commissioned by F5 Networks, financial services organisations across EMEA are increasingly exposed to and concerned about the rising menace of web fraud threats.

It can be painful for an organisation to admit that their systems have been breached by a cyber-criminal. However, as cyber-attacks become more aggressive, it is essential that data on cyber-criminality is shared and analysed. It may be that sharing this data, even among competitors, will be the key to protecting our most sensitive information.

As mobility becomes essential in business operations, enterprises need to decide how to handle their employee base when it comes to device usage in the workplace. Be it employer-provided devices or BYOD, enterprise mobility plans need to be both robust and adaptive.
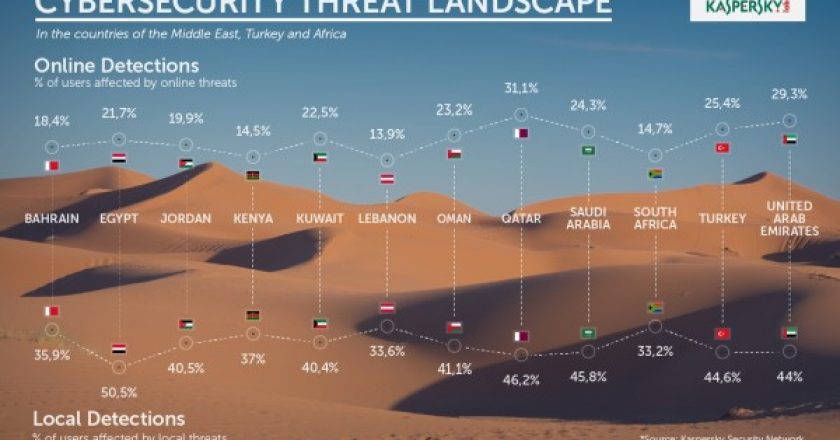
Kaspersky Lab’s Cyber Security Weekend for the Middle East, Turkey and Africa which took place April 26-29 in Lisbon, Portugal and brought together specialists from the Kaspersky team, an expert from EY, journalists and business guests.
ESET has unveiled its new ESET Retail Partner Programme for the Middle East to drive sales of home user management. The scheme …
Help AG, participated at the recently held GISEC 2015, where they took part together with six of their vendor partners.
The company entered into strategic distribution agreements with leading IT security vendors Shavlik, Fidelis and Niksun.

Cisco today unveiled a host of new capabilities and services that give security professionals extensive intelligence and analysis on potential compromises and solutions to protect against, respond to and recover from attacks.
The security company intends to leverage the event to educate regional businesses and CXOs on its patented Layer 8 technology and shall showcase how IT and security teams in the region can benefit from Cyberoam’s network security innovations.

Philippe Roggeband, Business Development Manager, Cisco Security Architecture, discusses the need for thorough security measures when it comes to the Internet of Things.

In the next few years, businesses may live or die by IoT. Handle it well and your company thrives. Mess …

An otherwise unremarkable hacking group likely aligned with China appears to be one of the first to have targeted so-called air-gapped networks that are not directly connected to the Internet, according to FireEye.

Palo Alto Networks has revealed details of a widespread vulnerability in Google’s Android mobile operating system that allows attackers to hijack the installation of a seemingly safe application – Android Package File (APK) – on user devices, replacing it with an app of the attacker’s choice.

Many recent studies of security vulnerabilities come to the same conclusion: The human factor is a greater risk to organisations than flaws in technology.

State sponsored malware is becoming increasingly sophisticated according to a report released by security vendor, Kaspersky Labs. According to a company statement, this new trend was confirmed during analysis of the EquationDrug cyber-espionage platform, the main espionage platform developed by the Equation Group.

There is no question that the use of mobile devices, both personally and professionally, are now not only convinient, but necessary for productivity. As the mobile technology develops, mobile security best practices must also adapt.

Researchers sponsored by the U.S. government have reportedly tried to defeat the encryption and security of Apple devices for years.

Cyber-terrorism attacks against power grids, water supply systems, chemical plants and other critical infrastructure loom as a threat that could become harsh reality before slow-moving agencies act to secure them better, says the head of Kaspersky Lab.
Bit9 + Carbon Black has announced a partnership with Microsoft to integrate some of the company’s endpoint solutions.