As Bitcoin’s popularity grows, so does talk about its standing as legal tender, but there are lingering issues that need to be sorted out before people start using Bitcoin to buy everyday things, experts said on Monday.


As Bitcoin’s popularity grows, so does talk about its standing as legal tender, but there are lingering issues that need to be sorted out before people start using Bitcoin to buy everyday things, experts said on Monday.

A Russian-speaking group is advertising “bulletproof” hosting for cybercriminals from data centres in Syria and Lebanon, an apparent effort to place new services in locales where Western law enforcement has little influence.

Thirteen people, including the creator of Blackhole, a popular exploit tool used to infect computers with malware, were arrested and charged in Russia with creating and participating in a criminal organisation.

The stakeholders of the channel gathered together for the second edition of Reseller Hot 50 Awards, which was held at H Hotel in Dubai.

When it comes to security, it seems everyone’s in a state of perpetual panic. Whether it’s mobile malware, BYOD or hacktivism, over the course of 2013 the issue of protecting valuable information and resisting attack has inspired a dizzying and persistent challenge.
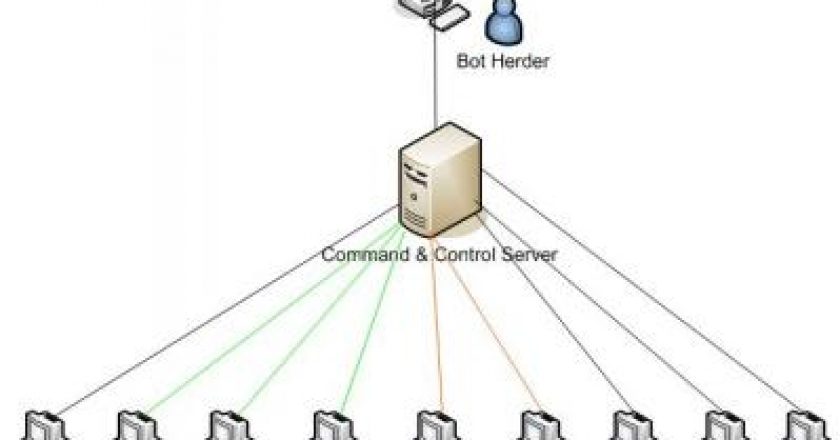
Two million logins and passwords from services such as Facebook, Google and Twitter have been found on a Netherlands-based server, part of a large botnet using controller software nicknamed “Pony.”

Balancing security priorities with business flexibility and agility is a tough challenge, says Anthony Perridge, EMEA Channel Director, Sourcefire.

Attackers are exploiting a new and unpatched vulnerability in Windows XP and Windows Server 2003 that allows them to execute code with higher privileges than they have access to.

A new Trojan programme that targets users of online financial services has the potential to spread very quickly over the next few months, security researchers warn.

Because data is often the most valuable corporate asset – especially when customer information is concerned – staying alert for potential compromise is a critical IT job. Unfortunately, looking into a potential data breach is not easy.

A new malicious software programme, advertised for sale on underground forums, claims to mine and steal bitcoins, according to a …

The U.S. National Security Agency reportedly hacked into over 50,000 computer networks around the world as part of its global intelligence gathering efforts, and also taps into large fiber optic cables that transport Internet traffic between continents at 20 different major points.

Spectrami and Fidelis XPS to reward its channel partners on the sale of Fidelis XPS across the region

Microsoft is opening a landmark 16,800-square foot (1,560m sq) Cybercrime Centre on its Redmond campus to act as an HQ and anchor point for a network of satellite offices that will collect evidence on malware from every continent, the firm has announced.

The creators of a Web-based attack tool called Angler Exploit Kit have added an exploit for a known vulnerability in …
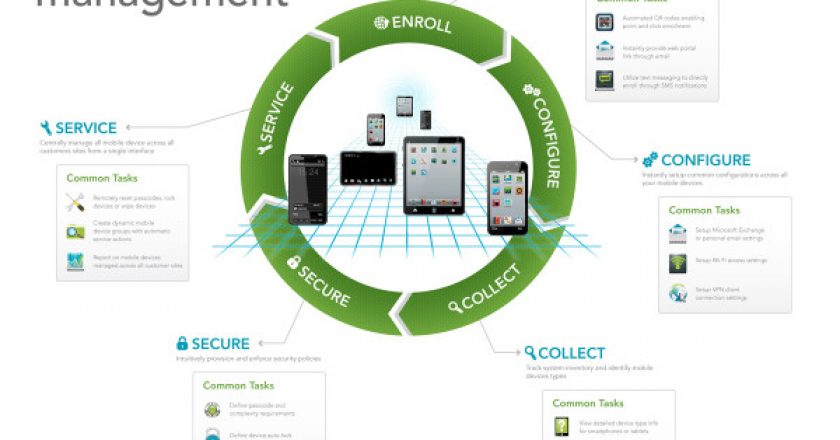
IBM yesterday announced an agreement to acquire Fiberlink Communications, saying the purchase is a key part of a broader mobile-security strategy to provide assurance in transactions conducted via devices such as iPhones and Android smartphones.

The website of a U.S. organization specializing in national and international security policy was compromised with malware that targeted a previously unknown vulnerability in Internet Explorer.

Security researchers have uncovered two unpatched vulnerabilities in Internet Explorer (IE) which have been exploited by attackers in an unusual “watering hole” campaign launched from a U.S.-based website that specialises in domestic and international security policy.

With some commentators labeling the BYOD trend as unstoppable, organisations are now turning to MDM to ensure the security of their networks. But how should MDM be tackled?

CNME is this week set to host its BYOD Summit 2013, the Middle East’s first technology to conference dedicated entirely to the bring-your-own-device trend.