Google is upping the rewards it offers to bug hunters on its Chromium Vulnerability Rewards (VRP) program to AED 18,365 ($5000) for those previously rated at AED 3,673 ($1,000), the firm has announced.


Google is upping the rewards it offers to bug hunters on its Chromium Vulnerability Rewards (VRP) program to AED 18,365 ($5000) for those previously rated at AED 3,673 ($1,000), the firm has announced.

A significant global talent shortage is looming as companies seek to leverage Big Data for competitive advantage but struggle to …

Investing in anti-virus software is no longer enough to counter cyber attacks on vital data systems, especially if national security is at stake.

Android vulnerabilities make for some of the biggest security concerns of the moment, according to Trend Micro’s Q2 2013 Security Roundup Report.
It may be old news now, but hackers are still using news of the royal baby’s birth to entice people into clicking on malicious links, according to researchers at Trend Micro.

If US intelligence agencies ban the computers of a Chinese company from classified networks should companies also avoid the same products? What if the vendor is one of the world’s largest PC makers?
The TOR Project is advising that people stop using Windows after the discovery of a startling vulnerability in Firefox that undermined the main advantages of the privacy-centered network.

Distributed Denial of Service (DDoS) attacks are getting bigger, but their duration are getting shorter, according to an analysis released …

A Home Affairs Select Committee has stated that the UK is losing the war on online criminal activity and that the government is too complacent in targeting cyber criminals.

F5 Networks says its BIG-IP 10200v with Advanced Firewall Manager (AFM) can handle traffic at 80-Gbps rates while screening and protecting tens of millions of connections, and simultaneously load-balancing server traffic.

With the major developers of banking malware laying low, a new crook on the block has emerged gunning to be top dog in the market.
Cyber-criminals are compromising websites at hosting companies at an ever-furious rate.

The impact of hacked SIM cards, one of the few stalwarts in the high-tech industry that has not seen a serious exploit, could be monumental.

The vulnerability was reported Thursday to Oracle along with proof-of-concept (PoC) exploit code.
Ransom attackers have finally made the jump from Windows to the Mac with news of a stunningly simple hack that tries to trick browser users into paying a $300 (£200) fine using a simple JavaScript routine.

Despite the significant Java security improvements made by Oracle during the past six months, Java vulnerabilities continue to represent a major security risk for organisations.

A new version of a file-infecting malware program that’s being distributed through drive-by download attacks is also capable of stealing FTP (File Transfer Protocol) credentials.

The Chinese cyber-spies behind the widely publicised espionage campaign against The New York Times have added Dropbox and WordPress to their bag of spear-phishing tricks.
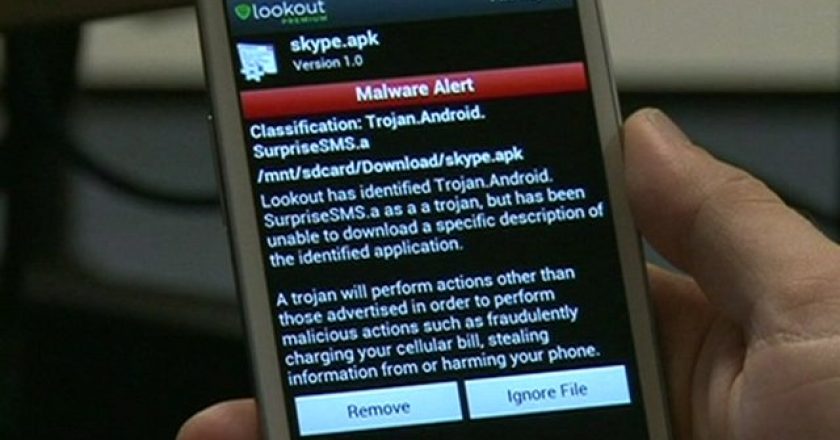
The number of mobile malware apps has jumped 614 percent in the last year, according to studies conducted by McAfee and Juniper Networks.

A second vulnerability that can be exploited to modify legitimate Android apps without breaking their digital signatures has been identified and publicly documented.