Mohamad Rizk, Regional Director, Middle East & CIS at Veeam Software, has penned his technology predictions for 2024, and has …


Mohamad Rizk, Regional Director, Middle East & CIS at Veeam Software, has penned his technology predictions for 2024, and has …

There is tremendous opportunity ahead and those that do so with future-proof technology will be most competitively placed to capitalise on the benefits.

Google Cloud has released its annual Cybersecurity Forecast report for 2024, compiling forward-looking thoughts from security leaders and experts from …

They are not just jargon; it is fundamental to securing your digital world. To succeed in the Middle East’s dynamic digital landscape, embrace TLS at the higher assurance levels with open arms.

Sherif Mansour, Banking and Capital Markets Transformation Director, Middle East & Africa, DXC Technology, has penned an exclusive opinion piece …
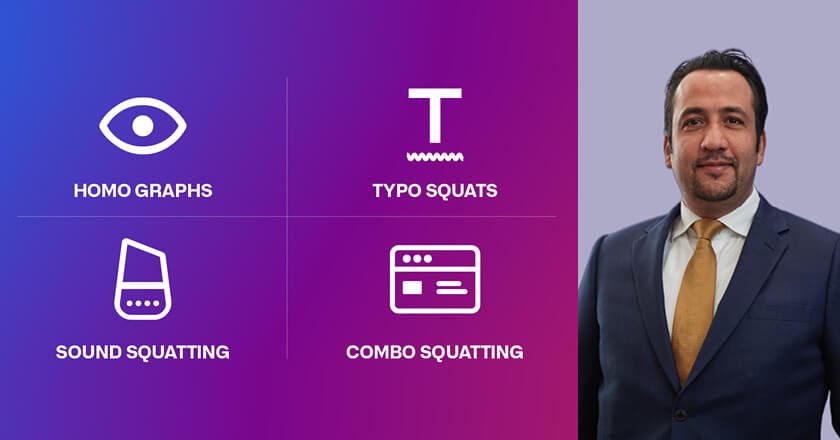
Detecting and not falling prey to these kinds of attacks are crucial, but the ability to takedown lookalike domains is equally important. Lookalike domain attacks are increasing in sophistication and prevalence, making specialized solutions like DNS security a must-have for all.

Vectra AI, Inc., the leader in hybrid attack detection, investigation and response, has announced the release of its annual threat …

In 2024, the telecommunications industry will continue to focus on technologies such as cloud computing, standalone 5G, AI, and the Internet of Things (IoT) to offer better speed, scalability, and innovation.

Kunal Badiani, Regional Head, MoEngage – Middle East, Africa and Turkey, on how critical evaluation involves asking relevant questions related …

Edwin Weijdema, Field CTO EMEA and Lead Cybersecurity Technologist at Veeam, has penned an exclusive op-ed for tahawultech.com, in which …

Nutanix is committed to helping partners drive customer success in the ever-evolving IT landscape.

Talal Shaikh, Associate Professor at Mathematical and Computer Sciences, Heriot-Watt University Dubai, writes an exclusive article for Tahawultech.com on the …

Vibhu Kapoor, Regional Vice President – Middle East, Africa & India at Epicor, has penned an exclusive op-ed for December’s …

James Harvey, CTO Advisor EMEA, at Cisco Observability, has reiterated the importance of brands of delivering seamless digital experiences this …