This 10-year goal for the EMEA region is part of Cisco’s global commitment to empower 25 million people with digital skills for long-term inclusion and economic resilience.


This 10-year goal for the EMEA region is part of Cisco’s global commitment to empower 25 million people with digital skills for long-term inclusion and economic resilience.

SAS, the analytics industry leader, asked leaders across the organization to give their predictions in business, technology, supply chains for …

CNME Editor Mark Forker spoke to Yazan Jammalieh, Regional Sales Director, Middle East, Turkey and Africa, at SCOPE to find …

CNME Editor Mark Forker spoke to Asef Sleiman, Sales Director at GBS, to find out how the IT company is …

A10 Networks and Gatepoint Research conducted a survey asking senior technology decision-makers about their experiences delivering applications in the cloud, including where their applications are primarily hosted; how they use their application delivery controller (ADC), and whether they’re satisfied with it; and what application delivery capabilities they need to ensure that their business objectives are successful.

CNME Editor Mark Forker spoke to Walid Gomaa, CEO of Omnix International to learn more about its solution offering designed …

IFS, the worldwide cloud enterprise software firm, has revealed the findings of its global research study, which uncovers the main …

Modernising internal procedures will not only increase overall efficiency, but will also leverage the power of modern solutions’ predictive analytic (AI) capabilities to make the best use of an organisation’s most valuable asset, its employees.

Significant advancement in its applications strategy, Cisco introduces industry-first Business Risk Observability, an enhancement of Cisco’s Full-Stack Observability application security solution.

IIIT Hyderabad uses the Choreo SaaS application development suite to provide “one-stop-shop” access to digital research projects that non-profit organisations can productise for their communities.
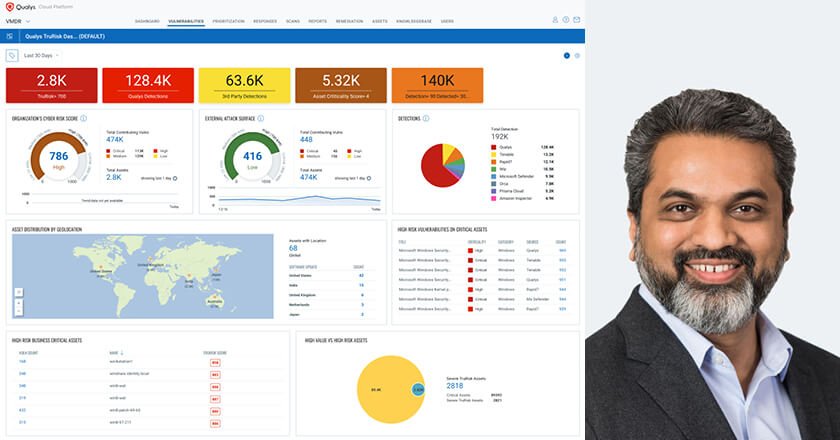
Introducing value-based, all-inclusive cybersecurity packages that include patch management and EDR to protect small and medium businesses from cyber threats.

The interplanetary metaverse project Everdome announces the first look at their ‘’Endurance Moon Skimmers,’’ one of their many in-world immersive multiplayer experiences currently in construction.

Ephrem Tesfai, Sales Engineering Manager META at Genetec reveals why the future of cloud is hybrid as it provides enterprises …

This Partnership will Aim to Further Protect Enterprises with External Attack Surface Management (EASM).
P&A’s role is expanding to encompass a cross-functional, comprehensive view of the business and it is now a key driver for tackling today’s business challenges and helping businesses keep pace with change.

Opens Regional Office in Riyadh, KSA.

Experts from analytics and AI leader SAS forecast the trends that will most impact financial services organisations in the year ahead.

Decentralised working requires thorough, secure DNS management.

Saudi Arabia’s AI powerhouse, Mozn joins forces with Deloitte to fight financial crime and bolster regulation across MENA.

AVEVA highlights world-leading digital solutions to help oil and gas companies in Egypt, North Africa and the Mediterranean achieve decarbonisation and value-chain innovation on the path to net-zero.
GET TAHAWULTECH.COM IN YOUR INBOX