At the 2014 Mobile World Congress, Nokia has released five new affordable handsets, including Nokia X, a family of smartphones …


At the 2014 Mobile World Congress, Nokia has released five new affordable handsets, including Nokia X, a family of smartphones …

WhatsApp’s voice calling service, planned for later this year to augment its hot text-message offering, could yield an influx of …

The Syrian Electronic Army has defaced the Forbes news website and publishing the names, email addresses and encrypted passwords of over a million of its users.
British intelligence agency Government Communications Headquarters (GCHQ) has reportedly infiltrated hacktivist groups and used denial-of-service and other techniques to disrupt their online activities.

Microsoft has finally concluded its protracted search and chosen its new CEO: Satya Nadella, who as executive vice president of the company’s Cloud and Enterprise group has successfully steered the shift of the company’s back-end server software and tools to the cloud.

The attack on Yahoo that started with the theft of user credentials from a third-party database highlights the risk of sharing usernames and passwords across multiple websites.

Yahoo reported a 6 percent drop in revenue for the fourth quarter as sales of its display and search ads dropped compared to last year.

SDN is a technology that promises to be the next big thing not only for IT organisations and networking vendors, but also for service providers, says Muhammad Rehan Sami, Senior Solution Architect, Business, Etisalat

SimpleAir is seeking $125M in damages from Google after a jury found that push notification services in Android infringe on a SimpleAir patent, the company said Tuesday.
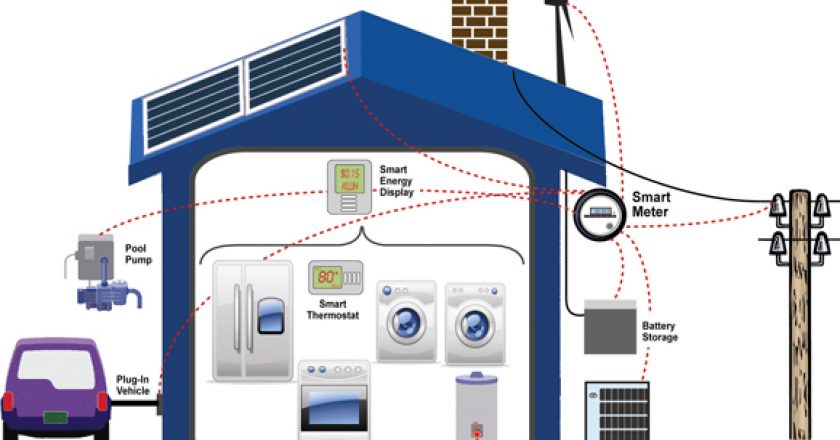
By 2017, the typical mobile user will share their personalised data stream with 100 applications and services every day, with wearable devices and Internet-connected appliances fueling the use trend, according to Gartner.

A list of 16 million email addresses and passwords has fallen into the hands of botnet operators, the German Federal Office for Information Security (BSI) said Tuesday.

The Syrian Electronic Army claimed credit for grabbing control of a pair of Microsoft company Twitter accounts and the firm’s primary blog for a short time Saturday.

Yahoo has started to automatically encrypt connections between users and its email service, adding an important security layer that rival Gmail has had for almost four years, but its implementation needs work, according to one security expert.
It has launched a flagship company website along with other social media sites such as Facebook, Twitter and LinkedIn.

Ford CEO Alan Mulally, seeking to end speculation over a possible move to Microsoft, told the Associated Press on Monday that he will not become the software company’s next CEO.

Kaspersky Lab experts have discovered that PC gamers around the globe were hit by 11.7 million attacks in 2013.

Skype said its social media properties were targeted, with the Syrian Electronic Army appearing to claim credit for the hacks.

Phone numbers paired with user names of over 4.6 million alleged Snapchat users were posted online by hackers, a few days after a security research group claimed a vulnerability in the social sharing service that could allow attackers to match phone numbers to Snapchat accounts.

Cast your mind back to the late 2000s – when the iPhone 3G beguiled consumers and the iTunes App Store began shifting users’ ideas about how they bought and used software. When Microsoft pros saw nothing but clear skies after Windows 7 cleared out the Windows Vista storm, and when green technology was touted as a transformative force in IT.

Oracle is gearing up to report its second-quarter earnings Wednesday and given the restrained expectations CFO Sandra Katz earlier set for key areas such as software revenue, Oracle’s results are sure to come under even more scrutiny than the tech bellwether already gets.