Microsoft today said that attackers are exploiting a critical and unpatched vulnerability in Office 2007 using malformed documents to hijack Windows PCs, and that Office 2003 and Office 2010 are also vulnerable.


Microsoft today said that attackers are exploiting a critical and unpatched vulnerability in Office 2007 using malformed documents to hijack Windows PCs, and that Office 2003 and Office 2010 are also vulnerable.
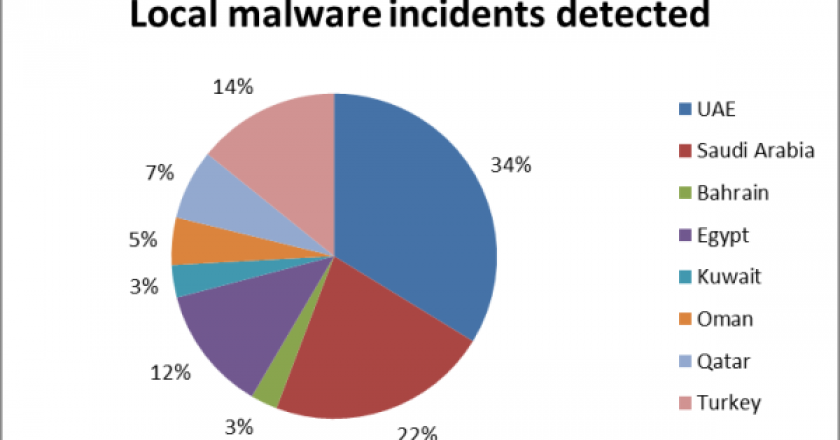
Kaspersky Lab has revealed research results that show an increase in malware in the Middle East.

The new products provide security without compromising system performance.

A study by analyst IDC shows how companies are using the open source Hadoop big data analytics systems alongside other systems to get value out of their data.

It is aimed at allowing private users to secure their PCs adequately in the region.

A British man has been charged with hacking into US government computers and stealing personal data about thousands of employees, then bragging about it on Twitter.
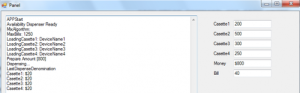
A malicious software program found in ATMs in Mexico has been improved and translated into English, which suggests it may be used elsewhere, according to security vendor Symantec.

Google said Wednesday it plans to reward developers for developing proactive security improvements for some of the most widely used open-source software programs.

As anticipated, the latest round of Microsoft’s Patch Tuesday monthly release of security fixes addresses a widely known Internet Explorer (IE) vulnerability already being exploited by malicious hackers.

The US National Security Agency has repeatedly tried to compromise Tor, the government-funded online anonymity tool, but has had little success, according to a new report in the UK’s Guardian.
With the addition of these services, Help AG strengthens its position

1) What is the main theme of your presence at GITEX this year? Huawei’s Enterprise Business Group will be the …

Ruckus Wireless aims to use the opportunity presented by GITEX 2013 to share its plans of expansion across the Middle East.

Two Middle East ethical hackers from Help AG, a regional information security consulting company, have qualified to participate in the World Finals of the Global CyberLympics, an EC-Council Foundation initiative supported by the United Nation’s International Telecommunications Union (ITU).

A group of between 50 and 100 professional hackers operating out of China has been systematically targeting businesses, military and government agencies around the world since at least 2009, security vendor Symantec said in a report released on Tuesday.

One of the world’s leading online security and privacy experts has warned that unprotected remote working and social media use can pose significant risks to both individuals and businesses across the Middle East.

Oracle added a feature in Java that lets companies control what specific Java applets are allowed to run on their endpoint computers, which could help them better manage Java security risks.

The Firefox OS, a new contender in mobile operating systems, will likely see HTML5-related attacks and assaults on a crucial …

Apple’s latest operating system iOS 7, due to be released Sept. 18, is already under the microscope of independent security …

A labor watchdog group is slamming one of Apple’s suppliers for allegedly exploiting its Chinese workers to build the upcoming budget iPhone.