Lax password implementation has meant that operational technology (OT) is now vulnerable to security attacks.


Lax password implementation has meant that operational technology (OT) is now vulnerable to security attacks.

Everything you have heard about cyber security is wrong, according to Gartner VP and distinguished analyst, John Girard.

Acting like a software version of a Transformer robot, a malware test app sneaked through Apple’s review process disguised as a harmless app, and then re-assembled itself into an aggressive attacker even while running inside the iOS “sandbox” designed to isolate apps and data from each other.

IBM has signed an agreement to acquire security company Trusteer, and plans to set up a cybersecurity software lab in …

Investing in anti-virus software is no longer enough to counter cyber attacks on vital data systems, especially if national security is at stake.

Android vulnerabilities make for some of the biggest security concerns of the moment, according to Trend Micro’s Q2 2013 Security Roundup Report.

Kaspersky Internet Security 2013 has been named the industry’s best home security solution by Dennis Technology Labs.
The TOR Project is advising that people stop using Windows after the discovery of a startling vulnerability in Firefox that undermined the main advantages of the privacy-centered network.
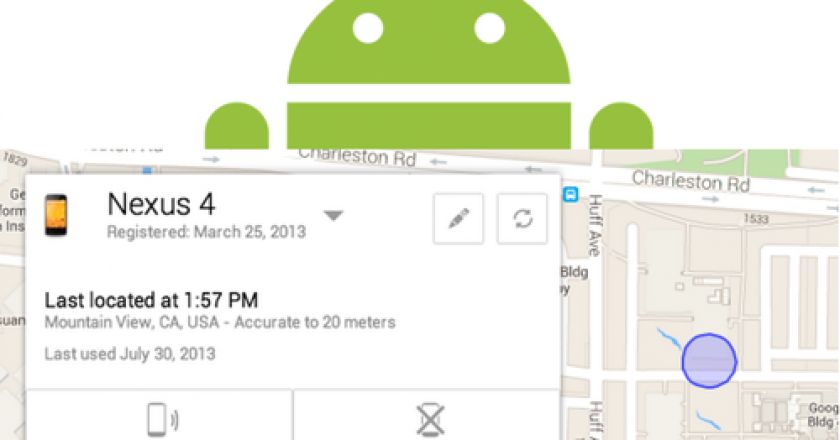
Fears about rogue apps and mobile malware may snag all the headlines, but when it comes down to brass tacks, …
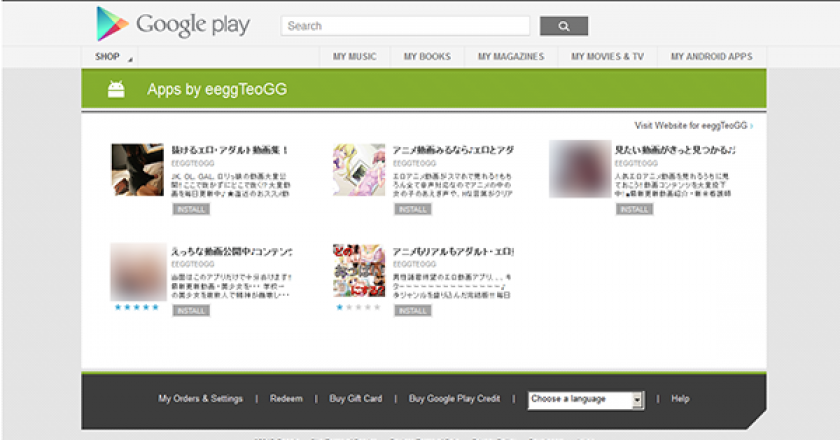
A steady stream of questionable applications is flowing daily into Google’s Play store for Android devices, according to security vendor Symantec.

Malware removed from forty percent of computers in those botnets, according to the vendor.

With the major developers of banking malware laying low, a new crook on the block has emerged gunning to be top dog in the market.
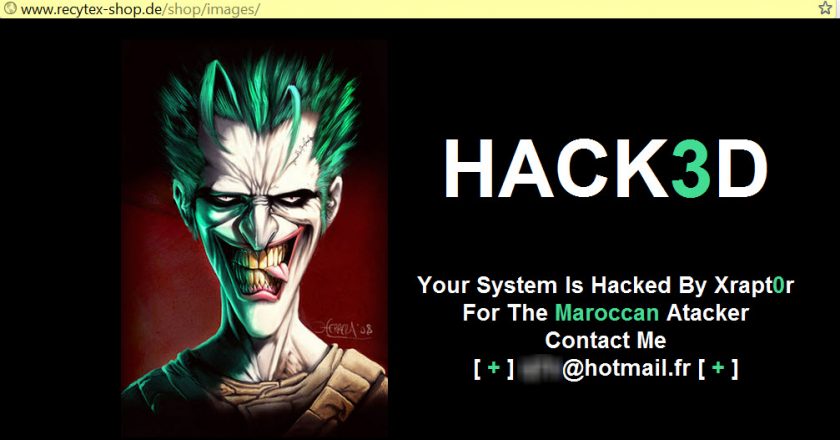
Cyber-criminals are compromising websites at hosting companies at an ever-furious rate.

Cisco is set to expand its security software portfolio with the acquisition of Sourcefire in a deal worth $2.7 billion.

An increasing number of Android phones are infected with mobile malware programs that are able to turn the handsets into spying devices.
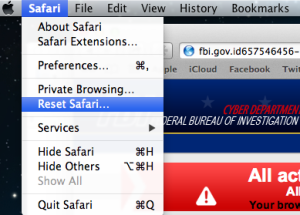
Ransom attackers have finally made the jump from Windows to the Mac with news of a stunningly simple hack that tries to trick browser users into paying a $300 (£200) fine using a simple JavaScript routine.

New research has shown that the vast majority of businesses are exposing sensitive corporate data to cyber-criminals by failing to implement effective BYOD strategies.

Symantec has discovered a bizarre ransom Trojan that eschews the usual demand for payment in favour of asking its victims to fill in an online survey to get an unlock code.

The Chinese cyber-spies behind the widely publicised espionage campaign against The New York Times have added Dropbox and WordPress to their bag of spear-phishing tricks.

Dennis Technology Labs said the most accurate product was Kaspersky Endpoint Security for Windows.