Security teams are so busy remediating cyberattacks that they don’t have time or resources to focus efforts on strengthening defences to deflect and protect against them.


Security teams are so busy remediating cyberattacks that they don’t have time or resources to focus efforts on strengthening defences to deflect and protect against them.

Talal Shaikh, Associate Professor at Mathematical and Computer Sciences, Heriot-Watt University Dubai, writes an exclusive article for Tahawultech.com on the …

Vibhu Kapoor, Regional Vice President – Middle East, Africa & India at Epicor, has penned an exclusive op-ed for December’s …

James Harvey, CTO Advisor EMEA, at Cisco Observability, has reiterated the importance of brands of delivering seamless digital experiences this …

Gil Vega, CISO at Veeam Software, has highlighted how cybercrime goes up by 30% during the holiday period, and has …

Wojciech Bajda, Managing Director, Public Sector Middle East and Africa, Amazon Web Services believes that Generative AI has the ability …

Toni El Inati – RVP Sales META & CEE at Barracuda Networks, argues that VPNs have had their day and …

Steven Kenny, Architect & Engineering Program Manager EMEA at Axis Communications, writes an exclusive opinion piece for Tahawultech.com on how …

Recently, AI-driven analytics and automation are fundamentally reshaping security operations, signalling a transformative future for the video surveillance industry.
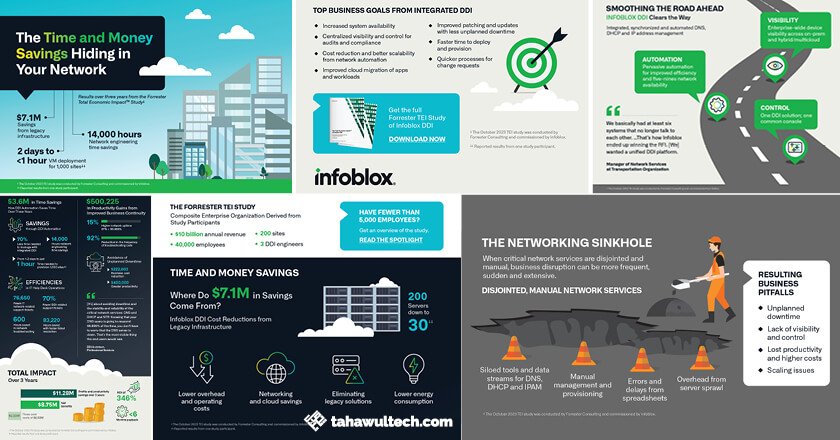
Infoblox-commissioned Total Economic Impact Study reveals how vulnerabilities in DNS are severely impacting enterprises’ bottom line.

In 2024, security leaders will begin the mindset shift towards turning incident management, patching, and evolving security protections into ongoing processes.

For Iraqi public and private organisations, safe and secure digital interactions can enhance the trust and confidence of users and customers, fostering innovation and competitiveness.

Lisa Wee, Global Head of Sustainability – AVEVA, tells CNME Editor Mark Forker about the role the industrial leader is playing in driving sustainability across the industry – the role AI can play in mitigating emissions, the need to validate data – and how we can create a net-zero mindset.

Kingston Technology insists latest counter-infringement products can repel threats and ensure hospitals and staff ‘protect the data they are entrusted with’.