HID Global has announced that its HID Approve two-factor mobile authentication and verification platform now supports Apple’s iPhone X Face …


HID Global has announced that its HID Approve two-factor mobile authentication and verification platform now supports Apple’s iPhone X Face …

Munich Airport has launched its Information Security Hub (ISH) – a competency centre where IT specialists with the airport operating …

Earlier this month, Google removed some 60 games from the Play Store after it was uncovered that a malware that was delivering inappropriate and malicious ads to kids.

The IT talent gap is driving up demand for skilled IT pros, but for certain roles and skillsets, finding — and signing — the right candidate can feel a bit like trying to capture a unicorn.

The effects of the net neutrality repeal are hard to predict, but there could be additional costs for using endpoint security tools if data rates rise.

Machine learning algorithms will improve security solutions, helping human analysts triage threats and close vulnerabilities quicker. But they are also going to help threat actors launch bigger, more complex attacks.

Hackers stole AED 3.86 billion from 3.72 million consumers in the UAE last year, according to the 2017 Norton Cyber …

Bulwark Technologies, a security specialised value-added distributor in the Middle East region, has announced that it will now offer solutions …

Computer defenders often spend time, money, and other resources on computer defences that don’t stop the biggest threats to their environment. What is causing this lack of focus in putting the right defences in the right places in the right amounts against the right threats?

D-Link and McAfee have announced the D-Link AC2600 Wi-Fi router powered by McAfee (DIR-2680), an all-in-one solution that automatically increases …

CES 2018 wasn’t just about electronics for consumers: It also saw the unpacking of a crate-load of products that can …

Hackers have targeted an attack at organisations involved in the Winter Olympics in South Korea and tried to access sensitive information, according to a report by cybersecurity firm McAfee.

In a statement, Intel says that the new vulnerabilities discovered by Google do not have the power to corrupt, modify or …

Cybercriminals are becoming more sophisticated and collaborative with every coming year. As with previous years, 2017 saw no shortage of …

ESET has recently launched its latest consumer security product portfolio for Windows. The new range is designed to protect against …
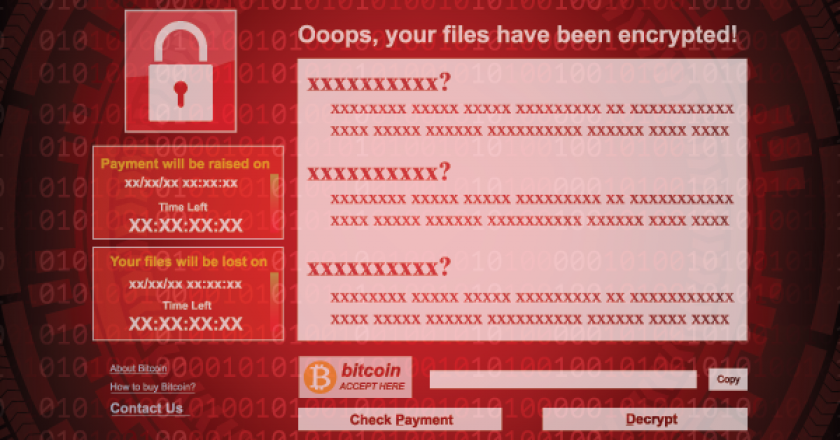
“After careful investigations, the United states is publicly attributing the massive WannaCry cyber-attack to North Korea,” said White House homeland security adviser Tom Bossert.

“The attack was widespread and cost billions, and North Korea is directly responsible,” wrote Homeland Security adviser to President Donald Trump Tom Bossert.

The number of new malicious files processed by Kaspersky Lab’s in-lab detection technologies reached 360,000 a day in 2017, which is 11.5 percent more than the previous year.

The campaign aims to educate customers – in particular the youth – on how to stay aware of deceptive and fraudulent activities on smart devices.

Lockheed Martin’s cyber kill chain approach breaks down each stage of a malware attack where you can identify and stop it.