Microsoft confirmed on Friday that it will continue to offer its malware scrubbing program to Windows XP users for more than a year after it stops patching the operating system.


Microsoft confirmed on Friday that it will continue to offer its malware scrubbing program to Windows XP users for more than a year after it stops patching the operating system.

A deeper look by Cisco Systems into the cyberattack that infected Yahoo users with malware appears to show a link between the attack and a suspicious affiliate traffic-pushing scheme with roots in Ukraine.
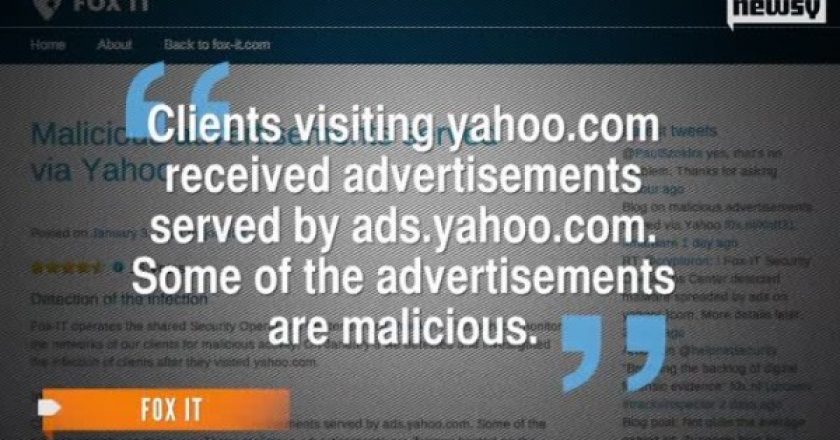
Yahoo said that malware spread by advertisements served by its European websites had not affected users in North America, Asia Pacific and Latin America as people in these locations did not receive them.

Trustwave’s SpiderLabs researchers have found a piece of malware that collects data entered into Web-based forms, pretending to be a module for Microsoft’s Internet Information Services (IIS) web-hosting software.

New attack campaigns have infected point-of-sale (PoS) systems around the world with sophisticated malware designed to steal payment card and transaction data.

Analyst firm A-V Comparative has released its November 2013 list of the antimalware programmes that do the best job of removing malware from an already infected system.

Researchers have demonstrated that microphones and speakers built into laptops can be used to covertly transmit and receive data through inaudible audio signals.

Cybercriminals are increasingly using the “Blackshades” malware program whose source code was leaked three years ago, according to an analysis by Symantec.

Through the advent of mobility, smartphones and tablets are now more dangerous devices to enterprises than laptops and PCs.
Mobile malware continues to proliferate, and at the same time employees are insisting on bringing their personal devices to work.

Malicious software aimed at stealing online banking credentials surged in the third quarter of this year to a level not seen since 2002, according to a new report from Trend Micro.

The FBI has offered large rewards for information that could help them catch a clutch of alleged cyber-criminals.

Microsoft today said that attackers are exploiting a critical and unpatched vulnerability in Office 2007 using malformed documents to hijack Windows PCs, and that Office 2003 and Office 2010 are also vulnerable.
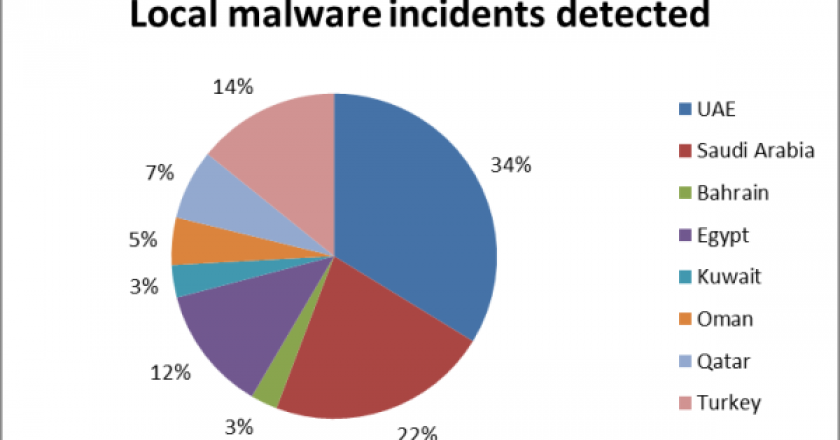
Kaspersky Lab has revealed research results that show an increase in malware in the Middle East.
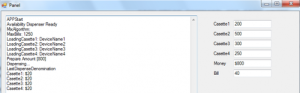
A malicious software program found in ATMs in Mexico has been improved and translated into English, which suggests it may be used elsewhere, according to security vendor Symantec.

Kaspersky Lab researchers identified Android malware threats that receive commands from attackers through the Google Cloud Messaging service.

FireEye could soon be known on the stock market as FEYE if its plans to go public in a $175 million bid made official with the SEC today come to fruition.

Highly organised Russian groups have transformed mobile hacking into an industrial scale business, a kind of “malware-as-a-service,” complete with marketing affiliates, distributors and customer support.
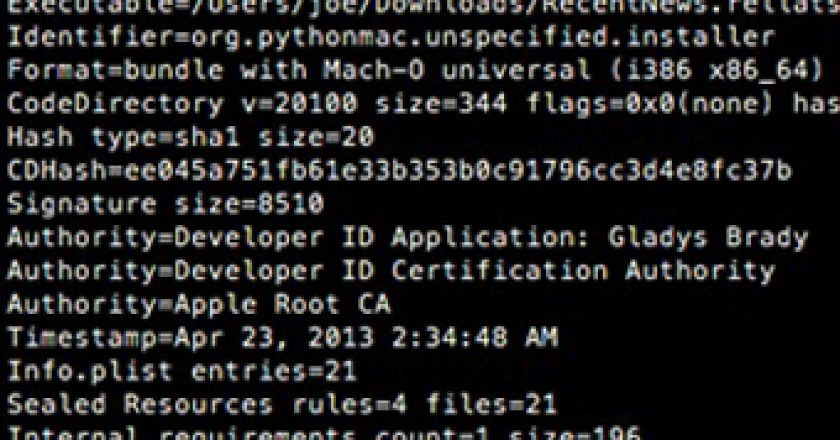
Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.

The first tools for injecting legitimate Android apps with open-source software that allows an attacker to control an infected smartphone remotely have been found in the criminal underground.

A new version of a file-infecting malware program that’s being distributed through drive-by download attacks is also capable of stealing FTP (File Transfer Protocol) credentials.