2014 has already gone down in history as the year of the data breach. As we move into the new year, what have we learned from our past that will aid us in the futures.


2014 has already gone down in history as the year of the data breach. As we move into the new year, what have we learned from our past that will aid us in the futures.

According to Kaspersky Lab, the company’s Global Research and Analysis Team has reported on seven advanced persistent cyber-attack campaigns (APTs) in the past year.

Data released by cloud storage service iDrive suggests that iPhone and Android users differ in terms of security and privacy habits as well as many others.
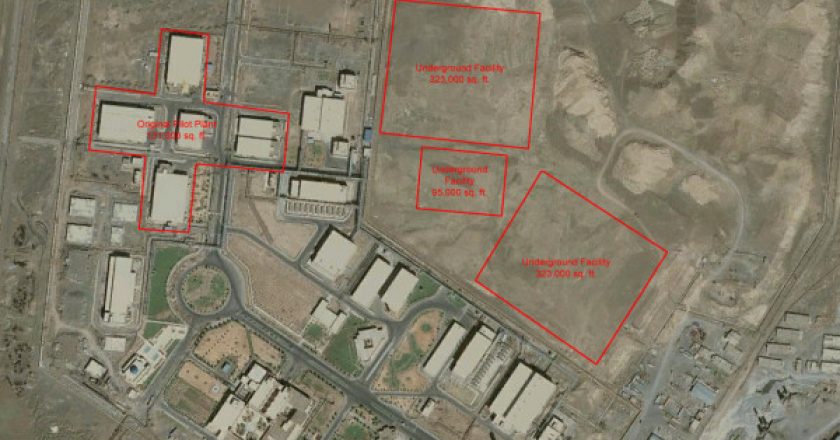
Stuxnet, the powerful malware that wormed its way in and hobbled Iran’s uranium enrichment efforts, infiltrated the secure networks of the nuclear program via trusted partners, newly public information reveals.

In addition to dealing with cybercriminals and hacktivists, enterprise security managers must pay increasing attention to avoid becoming collateral to nation-state cyber-warfare. Do recent high profile attacks on the region indicate that Middle Eastern businesses are at greater risk of attack, and what damage can cyber warfare inflict?
Epicor Software has announced that Kuwaiti firm Zenith Business Solutions is the latest value-added reseller to join its Inspired Partner Network in the Middle East.

With cybercrime an ever-present danger, hackers around the world attack user data for financial and political gain. But they are not all bad. CNME takes a look at the mindset of hackers good and evil, and how they constantly ask questions of governments and top companies.

The OS wars are nothing new. Every user has a laundry list of reasons why their operating system is king. One of the key points in determining which OS reigns supreme is security. CNME investigates the security successes and pitfalls of the most commonly used operating systems.

From paying bills on our smartphones to banking on our tablets, we are living more and more of our lives on our mobile devices. However, with all of this agility comes a measure of concern.

From April 20-24th, experts from Kaspersky Lab met with leading media in the region at the Kaspersky Lab Security Analyst Summit for the Middle East, Turkey and Africa held in Budapest, Hungary.

Virtualisation has made the data centre a more flexible and agile place. However, the trade-off in this software-defined shift is a measure of complexity when it comes to protecting our data. Enterprises must reconsider their protection strategy to reflect the new, virtualised world.
Scope Middle East today announced that it has been signed on by InfoWatch as a distributor for the Middle East region.

What do Middle East governments need when it comes to security, and are newly formed government entities set to revolutionise the way that states think about security?

With security so high on the agenda, businesses are doing everything they can to safeguard their networks from cyber-criminals keen to capitalise on software exploits. But do businesses pay enough attention to software updates when there are hundreds of other issues to address?

The world is still in the foothills of the cyberwar era but already online confrontation is being defined by an unstable and possibly dangerous mixture of proxy conflicts and old-fashioned espionage, mixed with lower-level digital activism, security firm FireEye has said.

And it was all going so well. As vendors began to build more comprehensive cloud-based product roadmaps, Middle Eastern users were beginning to see just how cloud services can streamline their businesses. According to a Gartner report from earlier in the year, cloud adoption was due to grow monumentally in the region up to 2016. This was largely due to issues surrounding security and compliance being ironed out.

The stakeholders of the channel gathered together for the second edition of Reseller Hot 50 Awards, which was held at H Hotel in Dubai.

When it comes to security, it seems everyone’s in a state of perpetual panic. Whether it’s mobile malware, BYOD or hacktivism, over the course of 2013 the issue of protecting valuable information and resisting attack has inspired a dizzying and persistent challenge.

Google has removed an application from its Play store that purported to be AdBlock Plus, a well-known application that blocks online ads.

Can the big cloud vendors work around the allegations of NSA surveillance, or is there a gloomy outlook for cloud in the region?